Modern cybersecurity isn’t harder—it’s finally convenient. Here’s why.
Introduction: The Access Problem Is Solved. Most Just Don’t Know It Yet.
Access control has always been one of the messiest, most misunderstood parts of cybersecurity.
VPNs. Password resets. BYOD risks. Shared logins. Conditional access policies that sound like a compliance thesis.
But here’s the thing—in 2025, the problem is no longer complexity. It’s awareness. Access control has quietly matured to the point where security can be frictionless. You just need to stop doing it the hard way.
At Next Perimeter, we believe access control should be invisible to users, backed by strong defaults, and built into every device, identity, and login—without requiring your IT team to reinvent the wheel.
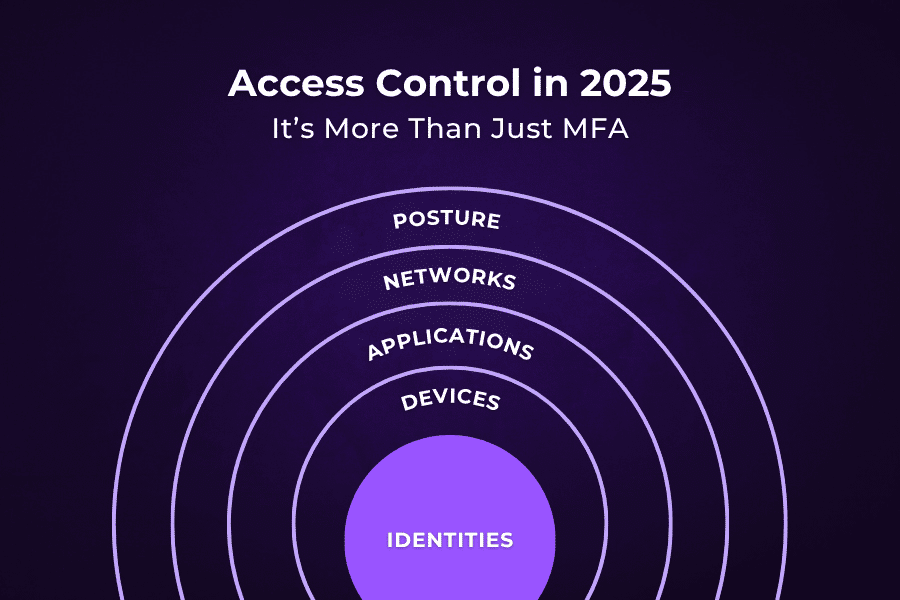
What Access Control Means in 2025
Access control isn’t one tool. It’s the combination of who you are, what you’re using, where you are, and what you’re trying to access.
We define it as a modern framework that includes:
- Identities: Azure AD (now Microsoft Entra ID), Google Workspace, SSO tools
- Devices: Laptops, phones, tablets—trusted vs. unknown, managed vs. BYOD
- Applications: SaaS platforms, internal tools, Microsoft 365, etc.
- Networks: Office, home, public Wi-Fi, foreign IP addresses
- Posture: Is your device patched, encrypted, monitored, and compliant?
This approach is foundational to our zero trust architecture. Every access attempt is evaluated—not just authenticated. And it’s enforced through a blend of cloud identity, device telemetry, behavioral analysis, and automated policy enforcement.
Let’s explore how each pillar of access control works in a modern, cloud-first environment—and how we’ve already operationalized these at Next Perimeter.
Identities: The New Perimeter of Every Business
In a zero trust world, identity is the new firewall. If you get identity wrong, nothing else matters.
At Next Perimeter, identity access starts with:
- Modern Identity Providers (IdP) like Microsoft Entra ID or Google Workspace
- Multi-Factor Authentication (MFA) enabled for all accounts
- No legacy authentication protocols, which are a frequent entry point for attackers
- Role-based access templates, so new hires inherit the right permissions by default
- Privileged Access Management, isolating global admin access and logging all actions
We don’t just monitor identities—we manage how, where, and when they’re used. If a login occurs at 2 a.m. from Kazakhstan, the device isn’t compliant, and the user hasn’t authenticated recently, that session is blocked automatically.
Every identity is scored, monitored, and constrained—because compromise starts with the wrong person getting access to the right thing.
Devices: Trust No Endpoint Without Proof
Identity is step one—but without a trusted device, your access control falls apart. That’s why our lifecycle-managed devices meet strict standards before they’re allowed into the system.
All devices must:
- Be encrypted and patched
- Run Elastic EDR and Defender for Endpoint
- Be enrolled in MDM or policy-based management
- Support Windows Hello biometrics (fingerprint or facial recognition)
For BYOD, we take a different approach:
- We allow app access via MAM (Mobile Application Management)
- We block downloads, sync, and file access
- We ensure no company data lives on personal devices
This lets employees check email or jump into a Teams meeting from their phone—but they can’t download financial spreadsheets to their camera roll.
Your device doesn’t need to be corporate-owned—but it does need to follow the rules.
Applications: Gate Everything, Not Just Admin Tools
Most breaches don’t happen because someone accessed a firewall—they happen because someone accessed the wrong application.
That’s why we treat all applications as gated zones, not open doors:
- Sensitive apps (finance, HR, admin portals) require trusted device + compliant posture
- SaaS discovery helps identify shadow IT and revoke unsanctioned access
- App-level conditional access limits what can be seen and done, depending on role, location, and context
- SSO (Single Sign-On) ties everything to identity—not stored credentials
And yes—we monitor access to low-risk apps too. Why? Because attackers start where you’re not looking.
Every app is gated by policy—not privilege—and tied to your identity context.
Networks: Geography Still Matters in a Cloud-First World
In 2025, most companies are cloud-native—but the network still matters, especially when it comes to location, speed, and threat exposure.
We enforce access policies based on:
- IP reputation and geographic location
- Network trust status (corporate vs. unknown Wi-Fi)
- ZTNA (Zero Trust Network Access) via our SASE platform
- Blocking all access from high-risk countries or VPN spoofers
For managed clients, we replace legacy VPNs with our built-in secure agent. Users don’t log into a tunnel. They log into our zero trust perimeter, where every packet is filtered before reaching the cloud.
We don’t care where you are—we care whether your access attempt makes sense.
Posture: Real-Time Trust, Not One-Time Checks
Access control isn’t a one-time “yes or no.” It’s a real-time evaluation of risk—backed by posture management.
We use posture signals from:
- Endpoint detection tools (EDR)
- Patch status and OS version
- Encryption enforcement
- RMM/MDM telemetry
- Suspicious behavior patterns (e.g., MFA fatigue or new logins from foreign regions)
These signals determine:
- Whether to allow, block, or prompt for step-up authentication
- When to trigger SOAR playbooks
- When to disable a session or revoke a token
Posture tells us not just who you are—but whether we should still trust you.
Operational Maturity: We’ve Already Solved This
We meet a lot of companies trying to build access controls from scratch. They’re often overwhelmed, or worse—stuck in vendor demos and policy paralysis.
That’s why we’ve simplified it.
Every Next Perimeter client starts with our prebuilt Blueprints for access control enforcement. No guesswork. No DIY.
Here’s what you get by default:
- MFA enforced, with support for biometrics via Windows Hello and mobile push
- New users receive role-based access, scoped by Blueprint templates
- BYOD devices are supported via MAM—no access to files or downloads, just secure apps
- Legacy authentication is blocked, eliminating password-only entry points
- Geo-restrictions and IP risk analysis applied through Conditional Access
- Device trust required for sensitive apps or admin access
- Anomaly detection via SIEM and SOAR, alerting on suspicious behavior
Every new user starts secure—automatically. We don’t reinvent the wheel for each client.
Biometrics Make It Invisible
The biggest change since the last time you looked at access control? The hardware caught up.
Modern business laptops now ship with Windows Hello infrared cameras and fingerprint readers by default. This means:
- No more typed passwords
- Faster, stronger logins
- Seamless MFA experiences that don’t annoy users
We recommend biometric-ready devices as part of our Lifecycle Management Blueprint—because modern access starts with modern hardware.
If your users unlock their phones with Face ID, why are they still typing passwords to access financials?
What About Security-Only Access Control?
Even if we’re not your MSP, we can still help secure access through:
- Network monitoring and IP risk analysis
- Identity monitoring for unusual sign-in activity
- SOAR playbooks to isolate threats and revoke access
While we won’t have control over your devices or tenant, we can act as a watchdog across identities, endpoints, and SaaS logins—alerting you when something’s off and helping you respond faster.
What Access Control Isn’t (Anymore)
Access control today is not:
- Just about enabling MFA
- Just a Microsoft Entra setting
- Just for IT teams
- Just about blocking access
It’s about enabling the right people to work securely from anywhere, using defaults that are already proven. You don’t need to be an enterprise to enforce this level of maturity—you just need a partner who’s done it before.
Want to Know Where You Stand?
We offer a simple Access Control Readiness Assessment that shows:
- Where you’re exposed
- What policies are missing
- How to get modern access control without a heavy lift
It’s not part of our full PERIMETER Score, but it’s often the first step toward improving posture, simplifying IT, and reducing risk—without adding complexity.
Ready for Zero Fuss Access?
Let’s turn your access strategy into an operational advantage.
Book your Access Control Readiness Assessment
or
Download our 2025 Zero Fuss Access Control Checklist