For many small and mid-sized businesses, the server closet feels like a safe bet; tucked away on-site, humming along, holding the company’s lifeblood of files and financials. But beneath that familiar hum lies a silent drain on capital, time, and growth. Hidden costs pile up with every hardware refresh, license renewal, outage, and sleepless night your IT staff spends “just keeping the lights on.” What once looked like control has become a liability, leaving SMBs vulnerable to ballooning expenses, security risks, and business-stopping downtime. The truth? The server closet isn’t protecting your business; it’s holding it back.
The Hidden Costs of the Server Closet Model
The traditional on-premises server model seems straightforward: you buy the hardware; you own your data. However, the true total cost of ownership (TCO) goes far beyond the initial purchase. For an SMB, these “hidden costs” represent a significant and unpredictable drain on resources.
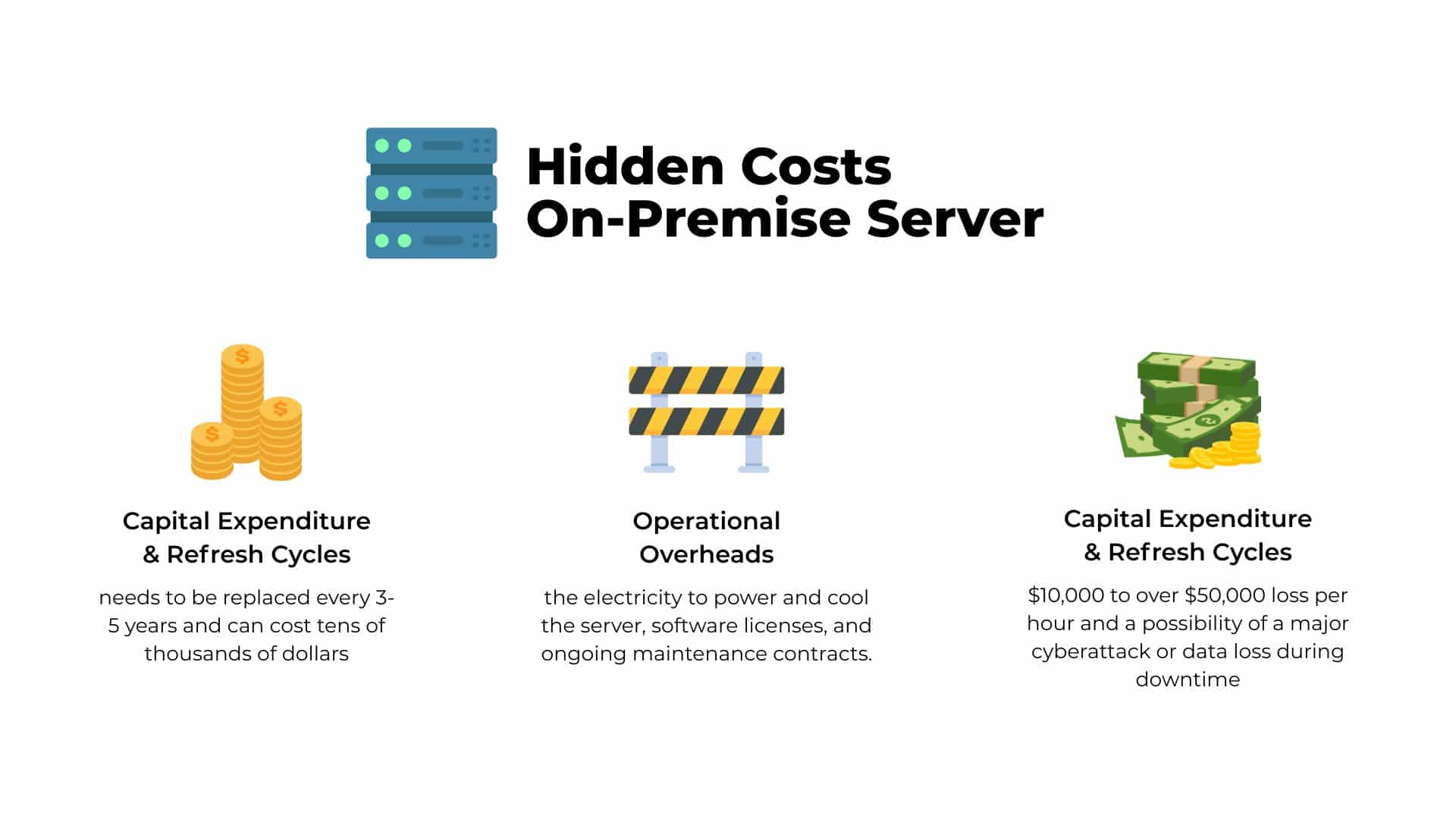
- Capital Expenditure & Refresh Cycles – A server isn’t a one-time purchase. It’s a capital expense that needs to be replaced every 3-5 years, creating a costly and disruptive refresh cycle. A single server upgrade can cost tens of thousands of dollars, a significant outlay for a growing business.
- Operational Overheads – Beyond the hardware, there are constant operational costs: the electricity to power and cool the server, software licenses, and ongoing maintenance contracts. Decommissioning a single server can save an estimated $500 annually in energy and 4-5 figures in maintenance alone.
- The Downtime Catastrophe – For an SMB, downtime is not an inconvenience; it’s an existential threat. When an on-premises server fails, the business stops. A 2024 ITIC report finds that for SMBs one hour of downtime costs between $127 and $427 per minute.
This model forces SMBs to spend precious capital and time on “keeping the lights on” rather than on initiatives that drive growth.
The “Serverless” Office: Consuming Services, Not Managing Hardware
The modern alternative is to eliminate the server entirely and shift to a model built on Software as a Service (SaaS). This isn’t just about moving files to the cloud; it’s a fundamental change in how IT is procured and managed. Instead of buying and maintaining a server for email, you subscribe to Microsoft 365 or Google Workspace. Instead of hosting a file server, you use SharePoint or OneDrive. This approach offers powerful advantages:
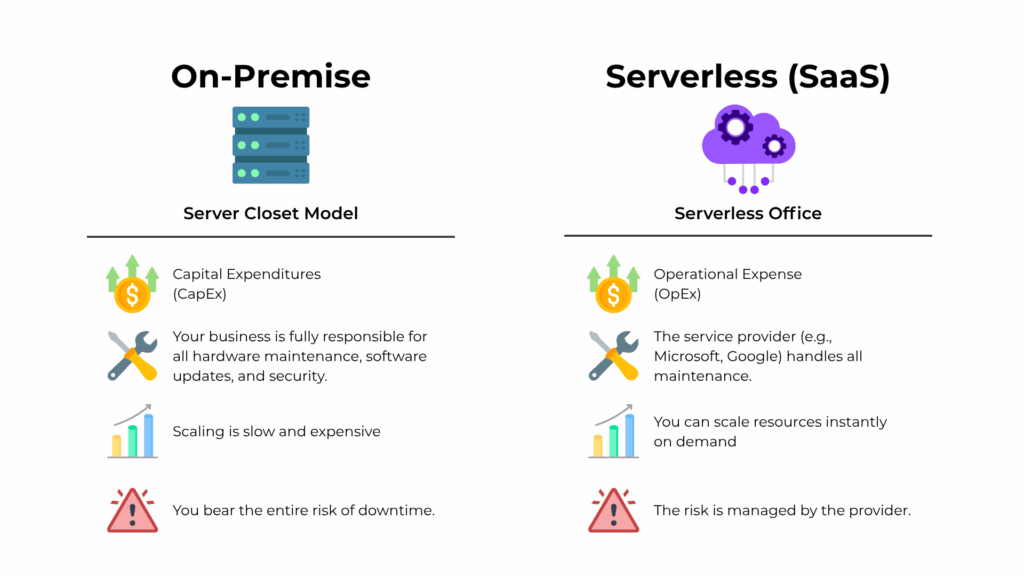
- Predictable Operational Costs – The serverless model converts large, unpredictable capital expenses into a predictable monthly operational expense (OpEx). This pay-as-you-go structure makes budgeting easier and frees up cash for core business activities.
- Automatic Updates and Maintenance – With SaaS, the provider is responsible for all hardware maintenance, software updates, and security patches. This eliminates the operational burden on the SMB and ensures you are always using the latest, most secure version of the software.
- Scalability on Demand – A serverless model allows your business to scale resources up or down instantly based on demand. Whether you’re hiring new employees or adjusting to seasonal business cycles, the technology flexes with you without requiring new hardware purchases. This shift allows an SMB to access enterprise-grade technology and reliability for a fraction of the cost and complexity of the on-premises model.
Identity Is Your New Perimeter
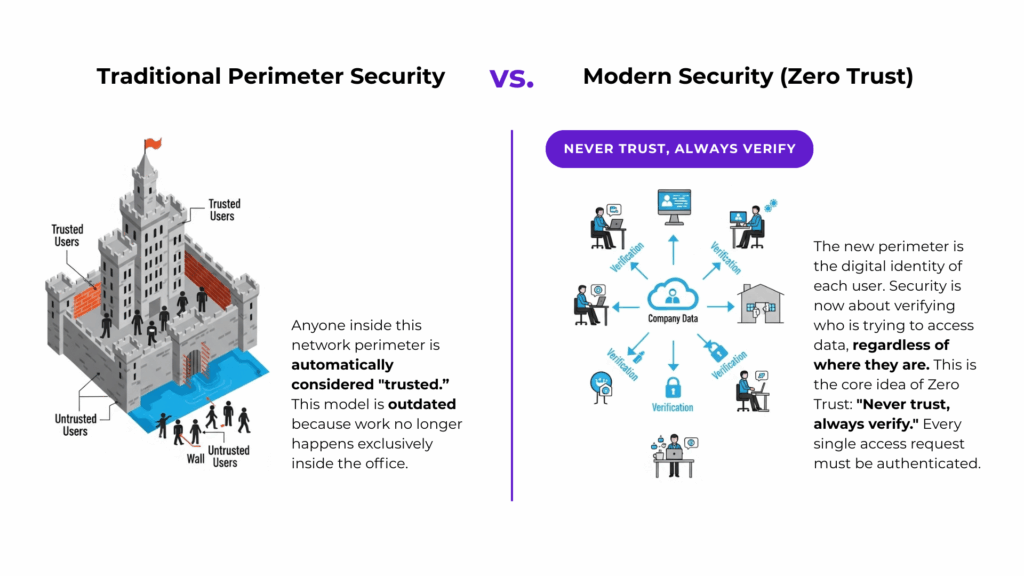
For decades, security was defined by a physical box: the firewall. This “castle-and-moat” approach assumed that anyone inside the office network was “trusted” and anyone outside was not. In today’s world of remote work, mobile devices, and cloud applications, that perimeter has dissolved. The new perimeter is not a location; it’s the digital identity of each user. Security is no longer about where you are, but who you are. This is the core principle of a modern security strategy known as Zero Trust, which operates on a simple but powerful mantra: “never trust, always verify”.
In this model, every single request to access company data must be verified, regardless of whether the user is in the office or working from a coffee shop. This fundamentally changes the security challenge. The goal is no longer just to protect data, but to manage and secure the access to that data. Your responsibility shifts from maintaining a physical firewall to ensuring that only the right people, using secure devices, can access the right information at the right time.
The Modern Security Blueprint for SMBs
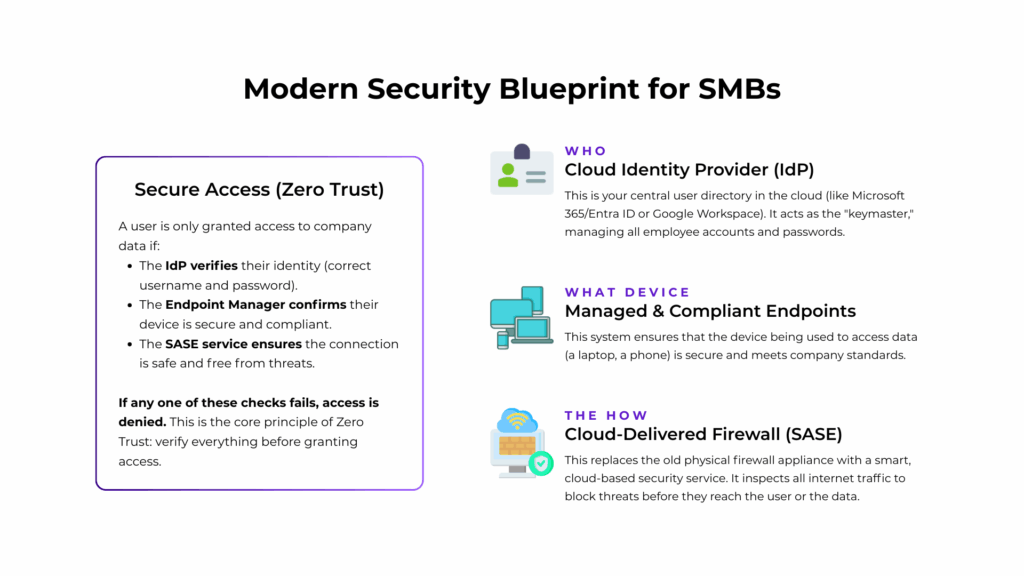
Achieving a Zero Trust security model where identity is the perimeter is not just for large enterprises. It can be implemented effectively by any SMB using a modern, integrated stack of cloud services. This blueprint is built on three interconnected pillars:
- A Cloud Identity Provider (IdP) – This is the foundation. Instead of a local Active Directory server, you use a cloud-native IdP like Microsoft 365 (with Entra ID) or Google Workspace (with Cloud Identity) as your single source of truth for all user accounts. This platform becomes the central “key master,” managing who has access to what. It uses modern, secure web protocols like SAML and OIDC to grant employees Single Sign-On (SSO) access to all their SaaS applications.
- Managed and Compliant Endpoints – Simply verifying a user’s password isn’t enough. A Zero Trust model must also verify the health and security of the device being used to access data. This is achieved through endpoint management tools like Microsoft Intune or Google Endpoint Management, typically in combination with an RMM/EDR solution. These tools ensure that every laptop and mobile device accessing company data meets your security standards. Those standards typically ensure that the device is encrypted, has up-to-date EDR, has a SIEM, and isn’t compromised. This device compliance status is fed back to the Identity Provider in real-time.
- A Cloud-Delivered Firewall (SASE) – The final piece is replacing the physical firewall appliance with a cloud-based security service. This architecture, known as Secure Access Service Edge (SASE), is essentially a firewall delivered as a SaaS solution. It inspects all traffic at the edge of the internet, close to the user, rather than forcing traffic back to an office. Crucially, the SASE service integrates with the other two pillars. It makes access decisions based on the verified identity from your IdP and the real-time compliance status of the endpoint, ensuring consistent, powerful security for all users, no matter where they are working.
The Ultimate Benefit: IT as a Growth Driver, not a Cost Center
For an SMB, the transition from a server closet to a serverless, identity-driven IT model delivers a profound strategic advantage. It’s not just about reducing hardware costs or avoiding downtime: it’s about enabling your team to work faster, more securely, and without constant technical roadblocks.
We’ve seen this shift firsthand. One of our clients, a Florida law firm, struggled with an outdated Virtual Desktop Infrastructure that slowed productivity and frustrated employees. By moving to Next Perimeter’s Modern Desktop Experience, they gained a secure, flexible environment that eliminated performance issues and kept costs predictable.
See how they made the shift—and what it meant for their bottom line. Download the case study or visit our Resources page to explore more case studies.
**************
By offloading infrastructure management, you free up your most valuable resources—time, capital, and talent—from the low-value work of maintenance and troubleshooting. Your IT focus shifts from managing servers to leveraging technology to solve business problems, improve processes, and innovate.
This modern approach levels the playing field, giving SMBs access to the same security, reliability, and scalability that was once the exclusive domain of large enterprises. It transforms IT from a necessary but burdensome cost center into a strategic engine for growth and a true competitive advantage.