Phishing emails feel like a new cybersecurity phenomenon, but they’ve been around for a while. We all remember the old Nigerian prince email scam. It’s become a punchline but, as The Washington Post has discovered, these scams are stealing billions of dollars from U.S. citizens. Though tactics have changed, and cybercriminals have become more sophisticated, the philosophy behind a phishing attack is still the same. Lure someone into handing over confidential information.
What is Phishing?
Phishing is a social engineering attack that lures a user into handing over confidential information by posing as a legitimate or trusted source. A cybercriminal will typically act as a business the victim uses or a manager from work. It doesn’t matter who the attacker poses as, all they need is to convince the target they are real.
For individual users, a phishing attack might lead to a bank account being compromised or identity theft. For businesses, it could lead to customer data breach, lawsuits, and loss of consumer confidence. Regardless of the reason, phishing attacks are devastating to anyone who is a victim.
Types of Phishing Attacks
Phishing attacks can be broken down into two types: Deceptive Phishing and Spear Phishing.
Deceptive Phishing
When people talk about phishing attacks, this is the kind they’re referring to. Deceptive phishing is the most common type of phishing attack. It’s popular among cybercriminals because of how easy it is to hit a lot of targets at once. When an attacker can send out thousands of emails at a time, only a few need to work for it to be successful.
An example is an email that looks like it’s from a customer’s bank. The message informs the target their account has been locked out after too many failed login attempts. It’s recommended that the user changes their password immediately. The email includes a link to a password reset page. The link directs the user to a spoof site, where the attacker collects any information the user enters.
Spear Phishing
Spear phishing attacks rely on deception more than numbers. A spear phishing attack targets specific people or organization. An attacker seeks out information on a person, or group of people, to customize the message to make it more believable. Information like the person’s name, phone number, title at work. A common source of information is LinkedIn, along with company websites or directories.
Effective spear phishing attacks are also the most simplistic. They mimic emails a user would receive daily while at work, so they don’t think twice about them. For example, an attacker will pose at the user’s boss asking for a particular file or payment of an invoice. For the target, this is a common request and doesn’t question its legitimacy. Before they know it, they’ve handed over confidential client or customer details or company financial records.
Anatomy of a Phishing Email
Deception is vital for a phishing attack to work. A fake email needs to look just real enough to appear authentic at a quick glance. However, with a little examination, you can pick a phishing email out of a lineup.
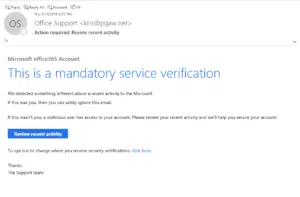
Here’s an example of a typical phishing email. In this one, the attacker is posing as Microsoft and is informing the target about recent activity on their account.
First, let’s go over a few things the attacker does to make the email look legitimate.
Subject Line: The email needs a believable subject line to get the user to open the message. An overly outlandish subject will raise a red flag, and a boring one will be sent to the trash. The sweet spot for an attacker is to craft a subject line that aligns with the person or company they’re impersonating. In this case, posing as Microsoft, the subject alerts the user that action is required on their account due to suspicious activity. An average user would want to know what’s going on with their account.
Content: Just like the subject line, the content of the email will align with the person or company the scammer is impersonating. It’s normal for a company like Microsoft to email users when there is a sign-in on their account on a new device.
Company Identity: To further the appearance of looking authentic, an attacker will use company branding in the email. Everything from logos and closing signatures to fonts and styling are at their disposal. Anything the user will quickly recognize and believe will be included.
Link/Button: A phishing email will have links scattered throughout. Typically, they will be hidden behind a button or text to hide the fact that it’s not a legitimate link. The link will send the user to a spoofed site that is a clone of an authentic site. In the example above, the site would look like the account sign-in page for Microsoft.
Next, let’s talk about what you can look for in a phishing email to spot the fake.
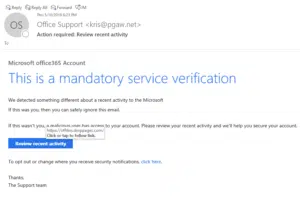
Poor Spelling/Grammar: One of the first things you’ll want to keep an eye out for in a phishing email is poor spelling and grammar. Any legitimate email from a corporation will go through numerous edits and be checked multiple times before being sent to customers. One mistake my slip passed the edits; numerous errors are a red flag. Now, scammers have been improving in this area, so you’ll want to pay close attention to what’s in the email.
Link URLs: Any scammer knows leaving an exposed URL will tip any user off to the fact it’s malicious. That’s why they do their best to hide them behind buttons, images or text throughout the email. People have a terrible habit of clinking a button or hyperlinked text without questioning them. If you hover over a button or hyperlinked text, a box will pop up showing where the link will go. In our example, clicking the button would send the user to “offdns.droppages.com.” Last we checked, that’s not a Microsoft site.
Sender Address: By now, we know that a scammer can fake or steal a lot of things in a phishing email. If they can’t fake it, they can hide behind a button or picture. What they can’t steal is an email address. To work around this, a scammer will manipulate their address to look as close to the real thing as they can. An omitted letter here and a swapped letter there will usually do the job. Other times, the attacker will use a random email address hoping that the user doesn’t notice, as shown in the example above.
How to Protect Against Phishing Attacks
End-User
As an individual, there are a few precautions you can take to reduce your chances of falling for a phishing attack.
The first is an increase in awareness. You need to be more critical of emails that show up in your inbox. Question the sender and motives behind the email. This includes messages from people you know. It’s better to be safe than sorry.
The second is attention to detail. We talked about the things to look for in a phishing attack. Paying a little extra attention to each email could save you from a catastrophic security issue.
Management
On the organization side, there are tools and practices available to combat a potential phishing attack. The two best ways to protect against a phishing attack are:
- Employee training
- An enterprise-level spam filter
Your employees are the primary targets of phishing attacks. Through proper training, your staff will be equipped with all the knowledge they need to spot and eliminate a phishing scam. Training gets your team thinking about the emails they receive every day.
The best way to prevent your employees from falling for a phishing attack is to stop the email from getting to their inbox in the first place. Spam filters are designed to do just that. If your employees take their training seriously, they’ll know they should flag any suspicious email they receive. The more emails your employees flag, the better the spam filter will get at identifying malicious messages.