How many of us have received an update notification and clicked the “remind me later” button? We’re busy at work and think “I’ll do it later,” or “it’s probably not important.” *click*
It happens to the best of us; however, this seemingly innocent event can have serious consequences for businesses.
Table of Contents
Patch Management Definition
Patch Management is the process by which businesses/IT procure, test, and install patches (changes in code or data).
Patches are intended to upgrade, optimize, or secure existing software, computers, servers, and technology systems that maintain operational efficacy or mitigate security vulnerabilities.
While simple in nature, most growing businesses struggle to identify critical patch updates, test and install patch releases to fix problems as they occur. In fact, the average time to patch is 102 days.
It’s no surprise that with over 16,500 security vulnerabilities reported in 2018, it’s virtually impossible for a small or medium-sized business with strained IT resources to keep up and protect your company.
Patch management is a time consuming and often misunderstood task, yet the impact can have devastating effects:
- 57% of cyberattack victims stated that applying a patch would have prevented the attack.
- 34% say they knew about the vulnerability before the attack.
The window between the disclosure of a vulnerability and exploitation has shortened forcing companies to race and deploy a patch before cybercriminals can compromise systems.
What are the different types of patches?
Software patches fix existing vulnerabilities or bugs as they are found after a piece of software or hardware has been released.
There are several types of patches:
- Hotfix – A hotfix patch is designed to fix a specific issue. Unlike typical patches, these hotfixes are developed and released as soon as possible to limit the effects of a software issue. Hotfixes can be applied while the software or system is still running (hot), without the need to restart or close the program. A hotfix may not be publicly disclosed.
- Point Release – A point release (also known as a dot release) is a small or relatively minor update intended to fix an error or flaw of a piece of software without adding features.
- Maintenance Release – Incremental update between service packs or software versions to fix multiple outstanding issues.
- Security Patches – A security patch is a change applied to an asset to correct the weakness described by a vulnerability. This corrective action will prevent successful exploitation and remove or mitigate a threat’s capability to exploit a specific vulnerability in an asset. Patch management is a part of vulnerability management – the cyclical practice of identifying, classifying, remediating, and mitigating vulnerabilities (security risks).
- Service Pack (SP) or Feature Pack (FP) – Major patches that comprise a collection of updates, fixes, or feature enhancements to a software program delivered in the form of a single installable package. These typically fix many outstanding issues and normally include all the patches, hotfixes, maintenance, and security patches released before the service pack. Most of us are familiar with Windows Service Packs, for example, Microsoft began rolling out the Windows 10 Version 1903 Update service pack on May 21, 2019, which became available to all users on June 6th. Microsoft Windows 10 Version 1903 introduced privacy setting updates, more control over how Windows updates are applied, a sandbox for professional users, password-less login, screen mirroring for Android phones, enhanced troubleshooting, and security features.
- Unofficial Patches – These patches are created by a third-party or a user community, most often because of a lack of support from the original software developer (e.g. the software company went out of business) or when a software product has reached its defined end-of-life. Like an ordinary patch, these are designed to correct bugs or software flaws. Nefarious individuals can introduce unofficial patches to create security vulnerabilities. While this is rare and quickly reported, we recommend only installing patches from trusted sources and for businesses to avoid unofficial patches.
- Monkey Patches – Similar to unofficial patches, a monkey patch (also known as a guerrilla patch) is an update designed to extend or modify the behavior of a plugin or software product locally without altering the source code.
What is the purpose of patching?
Patches are designed to repair a vulnerability or flaw identified after an application or software is released.
As we’ve learned, there are many types of patches. For this article, we’ll focus on official patches (hotfixes, point releases, security patches, and service packs).
Unpatched software can make the device a vulnerable target of exploits. Software patches are a critical component of IT operations and security.
How important is proactive patching to businesses?
We talk to small and medium business owners every day.
When we ask a prospective partner “how do you manage your system updates and proactive patching?” 8 out of 10 times, the answer is that the business does not have a formal patch management process, or “I don’t know.”
Let’s look at the world’s largest ransomware attack in history to understand how critical patch management is for the survival and operational effectiveness of your business.
The WannaCrypto (WannaCry) ransomware cyber attack was the perfect storm against individuals and businesses with poor patch management policies.
Even though Microsoft released a patch one month before WannaCry ransacked 200,000 computers across 150 countries causing damages estimated from hundreds of millions to billions of dollars in May 2017.
The cryptoware exploited a known vulnerability dubbed “ExternalBlue” allegedly developed by the U.S. National Security Agency. Unpatched computers were again targeted by the 2017 NotPetya cyberattacks for the same vulnerability.
Now years after the largest ransomware outbreak in history, attack attempts involving ExternalBlue continue to increase, reaching historic peaks according to ESET.
Why? Do we learn from the past?
Unfortunately, not everyone does, or individuals might not understand the critical threat patches prevent. For example, there are over 400,000 computers located in the United States that have not patched their systems to prevent hackers from exploiting this vulnerability.
Poor security practices and lack of patching are likely reasons why malicious use of the EternalBlue exploit has grown continuously since the beginning of 2017. This low hanging fruit is too attractive and lucrative for cybercriminals to pass up.
Patch Vulnerabilities by The Numbers
- 57% of data breaches are attributed to poor patch management. Source: Ponemon
- 37% of breach victims confirmed they don’t scan their systems for vulnerabilities. Source: Service Now + Ponemon Institute Study – Today’s State of Vulnerability Response
- 48% of 3,000 businesses surveyed reported one or more data breaches in the last two years. – Service Now + Ponemon Institute Study
- 34% of breach victims knew they were vulnerable before they were breached. – Service Now + Ponemon Institute Study
- 74% of companies can’t patch fast enough because they don’t have enough staff – Service Now + Ponemon Institute Study
- 65% of businesses state that it is difficult to prioritize patches. – Service Now + Ponemon Institute Study
- According to Edgescan, the average time to patch high-risk vulnerabilities increased by 22.9% from 64 days in 2017 to 83 days in 2018. Source: Edgescan Vulnerability Stats Report 2019
- 16,555 security vulnerabilities were released in 2018. Source: CVE Details
- 92%: Percentage of web applications with security flaws or weaknesses that can be exploited.
- 82% of employers report a shortage of cybersecurity skills, and 71% believe this talent gap causes direct and measurable damage to their organizations. CSIS – Cybersecurity Workforce Gap
Patch Management for Cybersecurity & Risk Mitigation
Prompt patching is vital for cybersecurity.
When a new patch is released, attackers use software that looks at the underlying vulnerability in the application being patched. This is something that hackers perform quickly, allowing them to release malware to exploit the vulnerability within hours of a patch release.
Security patches prevent hackers and cybercriminals from exploiting vulnerabilities that could halt operations. Imagine if a hacker encrypted all your data, servers and computers for a ransom.
Does your team have the resources, expertise, and recent backups needed to keep your business running?
By now, we should have a good grasp on how important an effective patch management procedure is to the cybersecurity of your business, clients and customers.
So, what does an effective patch management process look like? We’ll review below the patch management lifecycle below.
Patch Management Lifecycle and Process
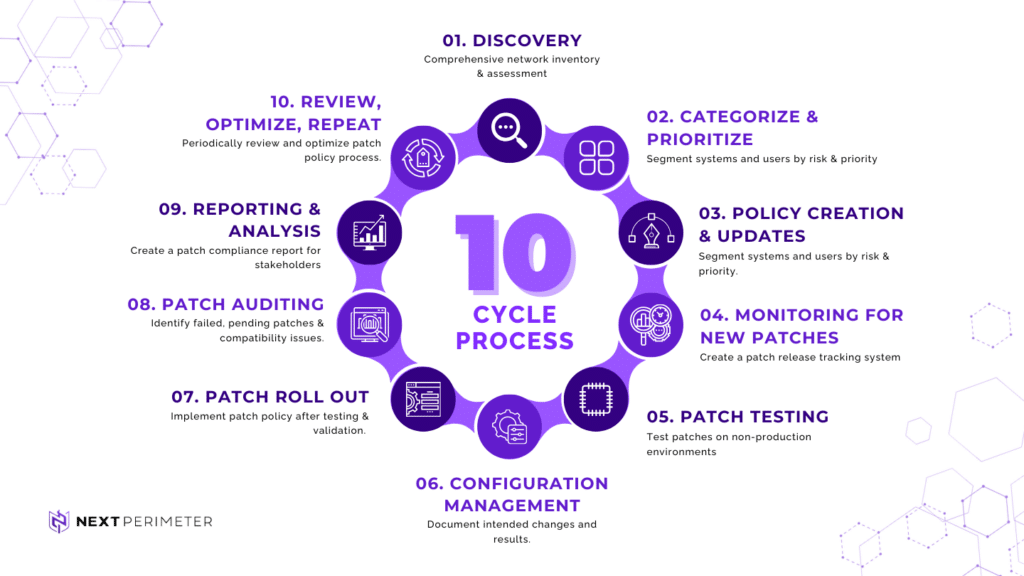
Step 1: Discovery
Before implementing a patch management process, any IT professional worth their weight will have a comprehensive network inventory or conduct an IT assessment to understand the types of devices, hardware, systems, operating systems, OS versions, and third-party software and applications in use across your business.
As businesses grow, IT resources become strained and it’s not uncommon for systems to become neglected or forgotten. Spreadsheets are difficult to keep up with and so internal IT may lose track of the many systems and programs in use.
Step 2: Categorization & Prioritize
Now that we have a good grasp on our IT environment and infrastructure, we need to segment the systems and/or users according to their risk level and priority. At the user-level, you might prioritize the C-Suite and users that frequently need to share, download, or install programs.
Specifically, we can rate users that frequently need to share documents over email or online as ‘high risk’ since they are more vulnerable from outside threats. Looking at hardware, you might prioritize the company’s server and business-critical hardware over a laptop that is infrequently used.
Step 3: Patch Management Policy Creation
Next, we develop patching requirements by deciding which systems, users, software needs to be patched, under what conditions and the frequency these systems/users need to be updated.
For instance, you might wish to make sure some systems or users are patched automatically and with greater regularity (liking patching employee laptops weekly) versus a server or network firewalls which might require more manual and less frequent updates.
Step 4: Monitoring for New Patches and Vulnerabilities
Modern businesses utilize a range of systems, software, and digital products, each with their own patch release and vulnerability disclosure schedules. While time-consuming, it’s vital that your team takes the time to catalog each technology vendor, their primary page used for vulnerability disclosures and product notifications (e.g. SonicWall Product Notifications).
Creating an organized patch release tracking system or notification feed will save your team hours (possibly days) over a year. Another example is “Patch Tuesday” for Microsoft who has a pattern of releasing patches the second (sometimes fourth) Tuesday of each month.
Step 5: Patch Testing
Before rolling out patches, especially on mission-critical elements like business servers, create a non-production test environment, deploy the patch, and monitor for incompatibility or performance issues.
If creating a test environment is not possible, we recommend testing patches on a small segment (two users) to assess if any adverse effects occur.
Step 6: Configuration Management
After the testing phase, document the intended changes and results. Should your rollout go awry, you’ll be able to quickly identify and troubleshoot unintended changes.
Step 7: Patch Roll Out
Now that your team has validated the patch(es), you will want to follow the Patch Management Policy established in step three to rollout as needed.
Step 8: Patch Auditing
Post-patch rollout, take a moment to identify any failed or pending patches. Monitor these for incompatibility issues. We recommend reaching out two a few tech-savvy end users that can help provide feedback if needed.
Step 9: Reporting
Each business unit has stakeholders, IT is no different. Prepare a monthly patch compliance report to share with the C-Suite and executives when needed. This will ensure everyone understands the importance of patch management and the fruits of your labor.
Step 10: Review, Optimize, and Repeat
As with most business processes – periodically review, update and repeat steps one through 9. Look for systems that have reached their End-of-Life (EOL), outdated hardware/machines, review policies quarterly, and revise as needed to ensure the effectiveness of your patch management policy.
Current Patch Management Best Practices
- Take a “Critical Updates First” approach and patch exploitable vulnerabilities as soon as possible. Critical vulnerabilities that have published exploit code should be given the highest risk rating in the Patch Management Policy.
- Implement a Data Backup & Recovery (Rollback) Plan. Every business should already have a Backup and Disaster Recovery plan, complete with on-site and off-site (cloud) full-system image backups. If your company does not, you can learn about the 11 key elements of an effective Disaster Recovery Plan in our recent post.With system image backups in place, your team can easily rollback any computer or servers that experience incompatibility or performance issues post-patch. These backups can save you hours, hard-earned money and frustration if anything goes wrong while rolling out major patches across the organization.
- Make proactive patch management a core practice of your policy. Taking a proactive approach to your patch management strategy will prevent your business from frequently going into emergency patching mode like many companies experienced with the WannaCry outbreak in 2017.Instead, by focusing on releasing patches as they occur, based on severity level, CVSS score, product name, and the prioritization model you created in step three above. This will allow your team to focus on strategic objectives that grow your business.
- Centralize and automate your patching process. While patching can be time-consuming, automated patch management allows you to save time and reduce errors.Most patch management software enables you to automate each stage of the patching process, from scanning applications of devices, downloading missing patches, scheduling and deploying patches based on designated policies to reporting.
- Utilize a Principle of Lease Privilege (POLP) approach for end-users. Many organizations often allow employees to have admin privileges with their company devices; this is especially common in the SMB space. What happens? Most employees will dismiss or ignore important updates, patches, and security vulnerability updates.A frequently overlooked patch management best practice that is to not give full admin rights to end-users. While it’s ultimately the responsibility of the IT department to execute a least privilege policy to restrict employees, end users really should only have a minimal amount of access or the privileges necessary to meet the demands of the role within an organization.
- Patch and update “golden images” at least once a quarter. “Golden images” are master software/system images used by IT as a template to set up and deploy new devices. When your company orders a new laptop or onboards a new employee, IT will often have a preconfigured system image that contains all the business applications, software, settings, privileges, and operating system necessary for the new user to hit the ground running. When your master images already contain the most up-to-date software and security patches, your team won’t have to do the same legwork again when setting up a new device.
Patch Management, Compliance, and Risk Management
As security breaches continue to increase, compliance regulations will continue to evolve to protect consumers. Government institutions, healthcare services and financial sectors are among the most heavily regulated, but other industries are rapidly creating their own security compliance rules and guidelines.
Implementing patch management is commonly required by security frameworks or standards, such as PCI DSS, CIS Critical Security Controls for Effective Cyber Defense, ISO 27001 Annex A, and NIST. In June 2018, the U.S. Department of Health and Human Services’ Office for Civil Rights (OCR) clarified in their OCR Cybersecurity Newsletter that promptly patching systems is a crucial element for covered entities and business associates to remain HIPAA compliant, going so far to explain that patch management is a requirement under – – 45 C.F.R. § 164.308(a)(1)(i)(A), 45 C.F.R. § 164.308(a)(1)(i)(B), 45 C.F.R. § 164.308(a)(5)(ii)(B) and 45 C.F.R. § 164.308(a)(8).
Due to the complexity of modern IT environments, the patch management process can be a major undertaking. However, failure to comply could potentially result in significant legal penalties for your business. Patch management ensures your business remains compliant and protects customers, consumers, and stakeholders. Here are a few compliance best practices you can implement to secure your business:
- Know who your vendors are and what security protocols they have in place
- Require certain levels of security compliance and protection from all third-party vendors, with a zero-tolerance policy towards vendors that fail to meet your security compliance standards
- Implement multi-factor authentication to reduce access to your environment via third-party connections
- Implement strict access control policies for your business applications, equipment, hardware, and software to reduce the risk of potential third-party vulnerabilities or tampering
Value of Working with Managed Patch Management Partner
A solid patch management process is an essential requirement for any size business. Unfortunately, most organizations do not have the expertise, software or mature processes/systems in place to effectively secure their infrastructure.
Manually checking for and applying patches in is almost an impossible task. Do you prioritize servers or employee workstations or third-party applications? Do you focus on security fixes or compatibility updates? And how do you keep track of which patches have been applied?
These are difficult questions for any IT team. IT teams are struggling to keep on-premises, data center, and cloud infrastructure up to date with the latest versions of operating systems, databases, and third-party applications.
Without the right investments in people, process, and technology, an organization can quickly fall behind on critical patches that address security and compliance requirements.
Rather than forcing already strained internal IT teams to update critical systems manually, many small and medium-sized businesses look to partner with Next Perimeter.
As a Managed Service Provider (MSP), we have the expertise, software, and mature systems in place to effectively secure your infrastructure using time-tested patch management processes that has evolved over 15 years.
We create a comprehensive Patch Management Policy for your business, use patch management tools to automate the mundane and have our engineers on standby to provide human intervention when needed to ensure that your entire network of devices, databases, servers, applications, and systems are protected.
Your business will remain up-to-date with latest features, functionality, security, and capabilities offered by application and OS vendors resulting in improved employee productivity, security, and compliance.
Automation provides an auditable change management process and helps plug exploitable holes in your security posture while complying with various regulatory mandates such as PCI DSS, HIPAA, NIST, FFIEC, GLBA, SOX, FERPA, and others.
Call Next Perimeter today to learn how our Patch Management solution reduces the risk of having a security breach and all the related problems that come with it, like data theft, data loss, PII and PHI violations, reputations issues or even legal penalties today at 888-286-4816.
Conclusion
- Patches are not an option; they are a requirement for secure to prevent security breaches, data theft, data loss, PII and PHI violations, reputation issues, legal penalties and ultimately protect your business.
- High-risk and critical security patches need to be deployed as fast as possible (within days) in order to prevent hackers from exploiting vulnerabilities.
- Hundreds of thousands systems and thousands of business could have prevented the WannaCry ransomware attack of 2017 had they deployed the security patches in a timely manner, saving hundreds of millions or billions of dollars in lost revenue and damages.
- 57% of data breaches are attributed to poor patch management.
- Prompt patching is vital for cybersecurity.
- End users should have the least amount of privileges necessary to fulfill their role.
- Patch management is a requirement of HIPAA and seeks to mitigate compliance or regulatory risks.
- Taking end users out of the patch management process will result in more secure environments.
- These aren’t OS-specific issues; everyone is vulnerable.
- Many small and medium-sized businesses work with Managed IT Services Providers to ensure an effective patch management policy is implemented.