Though it is an art form, there is no need for a Master of Fine Arts degree to enable MFA (Multi-Factor Authentication). Multi-factor authentication is a key to strengthening your business’s identity and access management.
Employees are both an organization’s best protection against cybercriminals and its biggest vulnerability. Instituting a second measure of security between your staff and data goes a long way towards each’s safety.
Multi-factor provides a layered defense, meaning that if one layer is bypassed, you still have another barrier in place. Traditional usernames and passwords are prone to brute force and dictionary attacks. MFA reinforces credentials.
So, what exactly is MFA, and how can it protect you? How is MFA instituted? Does it have any downfalls?
We will cover all of that and more in this article. If you already believe your organization’s cybersecurity is lacking, consider making an appointment for a cybersecurity consult with our Virtual CIO today.
What is MFA?
Multi-factor authentication is the addition of factors beyond traditional credentials to secure authorization.
Employees log in using their normal username and password. They are then opened to clear the second round of authentication. The second authentication factor could be anything from a randomly generated passcode to a retina scan. We will discuss different MFA techniques later.
These techniques generally come from three categories. Something the person knows, something they have, or something they are. Ideally, each level of authentication comes from a different category than the one before.
MFA is no longer just a recommendation for some businesses. Payment Card Industry (PCI) Data Security Standard compliance requires the use of MFA “for all remote network access that originates from outside the network to a Card Data Environment (CDE).” PCI-DSS version 3.2 requires the use of “all administrative access.”
The Federal Financial Institutions Examination Council began recommending using multiple factors when accessing online financial information, starting in 2005.
Difference between MFA and Two-Factor Authentication
When discussing MFA, keep in mind that MFA encompasses the dated term “Two-Factor Authentication.” Two-factor was used at the outset of the use of MFA when most organizations were only adding one more factor to their security.
For example, swiping your debit card at an ATM counts for “something you have,” with the debit card itself. When you enter your pin, that is “something you know.” Two-factors.
The mainstream term has moved toward “multi-factor authentication.” This is because more companies have consistently added biometrics, location, and/or time as a third factor.
Authentication vs. Authorization
Though they look like similar words, authentication and authorization are quite different.
Authentication is the process of verifying somebody’s identity. Authorization is verifying someone has access to a file, data, etc.
Authentication always comes before authorization. Before your security guard lets somebody into your building, you would want them to confirm the person is who they say they are, right? Once the person authenticates, the guard can authorize entry.
To determine whether someone is authorized to view a piece of data, you will want to consider leveraging access controls. Once you have determined what each user can access, you can set up their authentication to make sure they are identified.
Kinds of MFA
As we mentioned before, there are three main types of categories for authentication factors: What the user knows, has, and is.
There are new factors in play, as well. Where the user is, and when they are trying to log in can also be a great way to authenticate.
Let’s take a deeper look.
Things You Know
Here is the timeless classic. Whether you are logging in to a secret document, signing into your email, or entering a super-exclusive club – the question has always been the same.
“What’s the password?”
This is the quintessential “something you know” authentication. If you know the password, you are in an exclusive group.
But with enough guesses and the technology to fire them off faster than you can count, passwords can be cracked. A password is not enough nowadays. It must be long, have special characters, capital, upper and lower-case letters; not be a dictionary word, and more.
It is easy to see why you need more than just a password to be safe. Brute force and dictionary attacks are one thing, but sometimes those are not even needed. Sometimes employees set poor passwords.
Answers to personal security questions can be a second layer of “something you know,” but are subject to the same types of attacks. There are so many kinds of “first car,” “street you grew up on,” and “mother’s maiden names” that exist.
So, if modern technology can crack your password, they can crack your security question. Be sure to stay in tune with all password best practices, like using different passwords for each account and using a password manager.
Even better, use a second factor type.
Things You Have
Do you remember all the time you spent looking for the dungeon key in your favorite video game? How about all the frustration that came with going in circles before you found it?
Think of your second factor as the dungeon key. Except for this time, you are the keeper of the key, avoiding the frustration of finding it. It’s the same as a swipe-able access badge, keyfob, or just a regular key (known as hardware tokens).
In the case of your IT, the key will generally be your smartphone with a One-Time Password (OTP). Your OTP will either be generated by an authenticator app or sent to you via text or email. Often, this is done when you are looking to reset a password, as well.
Authenticator applications can also be referred to as “software tokens.”
Your OTP itself is something you know, but it can only be provided to you by something you have. Like that smartphone.
Things You Are/Biometrics
Biometrics are the use of human characteristics that authorize access. Think of the common ways that some smartphones unlock these days using your fingerprint or face.
For agencies that want to go a bit further, you can use retina or iris scans instead of face scans. Other physical attributes used for biometrics are hand geometry, earlobe geometry, and voice authentication.
An emerging use of biometrics for authentication is behavioral analysis. This is not just a physical manifestation of “things you are,” but the way you are.
Take for instance a digital signature scanner. Scanners authenticate a digital image of your handwritten signature against other instances of it.
A typing analysis does not take into effect what you type, but how you type it. How fast do you type? In what order? What common patterns emerge while typing certain groupings of words?
As crazy as it sounds, this behavior can be used to confirm your identity. The same can be done with the way you use your on-screen cursor. These more intense versions of biometrics are largely used in the financial sector.
Time and Location
The laws of physics can affect your IT access, just as it governs most everything else.
Do you remember that time when you walked into a bar in Tokyo, bought a few drinks, then immediately walked into a store in New York City to buy an umbrella? Probably not. It can’t happen.
This is why as soon as your bank notices similar transactions overlapping, they call you to sort it out. Just as your bank watches over your money, the same can be done with your data.
Any cybersecurity provider worth their weight will stop an account from authenticating in two physically impossible distances within an unreasonable amount of time.
Why Use MFA?
There is plenty at stake any time you need a credential. That is why you are protecting something in the first place. The fact of the matter is that enabling MFA is easy.
Billions of credentials are stolen over time. The proof is clear: cybertheft happens, and it happens often. Breaking passwords is easy, and there are many ways to do so.
Not to mention, passwords are simply handed over in many instances. Phishing emails are one of the most successful cyberattacks and do not even involve cracking a password. That is why cybersecurity training for employees is necessary from the top to the bottom of your organization.
If you are a business owner or a CEO, you must consider that your employees are your greatest cybersecurity liability. Employees will do the bare minimum, even when enforcing strict password requirements. At least one member of your team is liable to fall for a phishing email, and one credential is enough to get a cybercriminal into your data.
By adding a second authentication factor, bad actors who steal a credential will run into a second barrier. Without the possession or biometrics of an employee, they will not gain the access they crave.
Remote employees can cause a threat as well if they are using a non-corporate or unmanaged device. Often these devices are accessing your data remotely but lack the security measures of your corporate machines. If all device, network, or applications do not have adequate protection, cybercriminals have a backdoor to your data.
All in all, MFA is a reinforcement of your existing security measures. Adding secondary and tertiary factors only serves as beneficial. If you have a front door to your warehouse, you’ll want a lock. But what if you also add a fingerprint or face scanner, like your smartphone?
How many times do you open your phone a day? How easy is it, that you can open it that many times? That is the key to MFA: security in a simple form.
Limits of MFA
In early 2019, a Polish cybersecurity researcher named Piotr Duszyński revealed a tool called “Modlishka,” which used a reverse proxy to bypass MFA. He made the tool public to show that there are still risks that multi-factor authentication cannot fix.
It is important to understand that no security measures are 100% foolproof. Knowing your weaknesses is equally imperative no matter how reinforced your defenses are. Unfortunately, MFA has its downsides and can be defeated too.
The biggest downside is that account recovery often only requires one factor, even if security is set up to log in with two.
If one of your factors involves the use of a mobile device, there is a chance it could limit some users’ access.
Smartphones are not always completely reliable. Perhaps the battery is dead, or service is poor in your area. If you cannot access the internet for either reason, you will be locked out of your mobile-based authorization factors.
Things only get worse if that mobile device is lost or stolen. If a token or OTP is intercepted by a potential cybercriminal, they have broken that factor of authentication.
The same fate is possible if a user falls prey to a phishing attack. If they are redirected to a spoofed URL, there is a chance they hand over both their username/password combo and an OTP that can be used immediately.
There are other man-in-the-middle type attacks that can intercept credentials:
- Man-in-the-browser – Similar to a man-in-the-middle attack, the hacker specifically takes over controls inside a web browser
- SIM cloning – In this case, a hacker would take over a mobile device’s SIM card, copy its software, and take over that device’s functions.
- IMSI-catchers – Think of a man-in-the-middle attack but using a mobile phone tower instead of a browser or an operating system. Used for mobile devices to intercept OTPs or other tokens.
Many of these liabilities show why biometrics are being used at an increasing rate. Does it sound easier to steal a smartphone, or to steal a fingerprint? How about spoofing a URL vs. impersonating someone’s face, retina, or behavior?
Currently, the best way to reinforce your second factor is by using a hardware token with a universal second factor (U2F) standard.
How to simplify MFA
With extra layers of security, access will take more time. This can be frustrating for your users, but it is worth it in the end.
Here are some ways to simply your MFA while keeping hardened cybersecurity.
Single Sign-On (SSO)
Single sign-on (SSO) is a service that allows users to log on to many applications through a single set of credentials. SSO acts as a middleman, serving out a single set of credentials across the needed apps when the user sends an authentication request. Once signed in, users will not need to re-enter authentication.
SSO lessens the frustration of users who are constantly forgetting and resetting passwords. In this case, they need to remember fewer and they forget less often. With fewer opportunities to enter credentials, there are fewer chances for phishing attempts.
However, keep in mind that with SSO, if an attacker gets access to one app, they likely have access to all of them. A second factor will still be necessary.
Push Authentication
Most authenticators offer push notification authentication. Use this option instead of users having to log into an authenticator app, remember an OTP, and input it somewhere else.
This is like any notification you get on your phone, but all a user must do is hit “confirm.” If the push authentication is sent to your smartphone, you likely just authenticated your phone itself by using a biometric.
Push authentications bring more simplicity to authenticating. Sometimes they bring even more factors of protection into play.
Adaptive MFA
Adaptive MFA is the use of context to determine if a user authenticates against many real scenarios. Remember the example from earlier about making a purchase in Tokyo and New York City within minutes?
That is an example of Adaptive MFA. A set of rules, or the laws of physics in this case, are used to prove an authentication is false.
Businesses can set up their own rules to deduce a suspicious login attempt based on their operations.
Here is a simple example:
Say all your users work from the same physical office, never go on business trips, and are not permitted to work from home. The organization can prohibit authentication from other locations or IP addresses. Yes, this may seem like overkill, but it will certainly stop anyone not on staff from accessing data.
If your company only uses the same standard-issue computer across all employees, you can limit authentication to an OS of your choice. If a user tries to log in from an Apple OS, but your company uses Microsoft, authentication will fail.
These factors, combined with other examples, adapt to your business and provide an additional layer of protection. With the correct setup, organizations can tailor their MFA to all potential scenarios.
MFA in Microsoft 365
So, you’re ready to set up multi-factor authentication in your organization’s Microsoft 365 cloud. But how do you do it? What options do you have?
Setting up MFA in Microsoft 365 is quite easy. Using your Microsoft 365 portal, select users. Then click the multi-factor authentication button and choose the users for which you plan to enforce MFA. You must have global administrator privileges to do so.
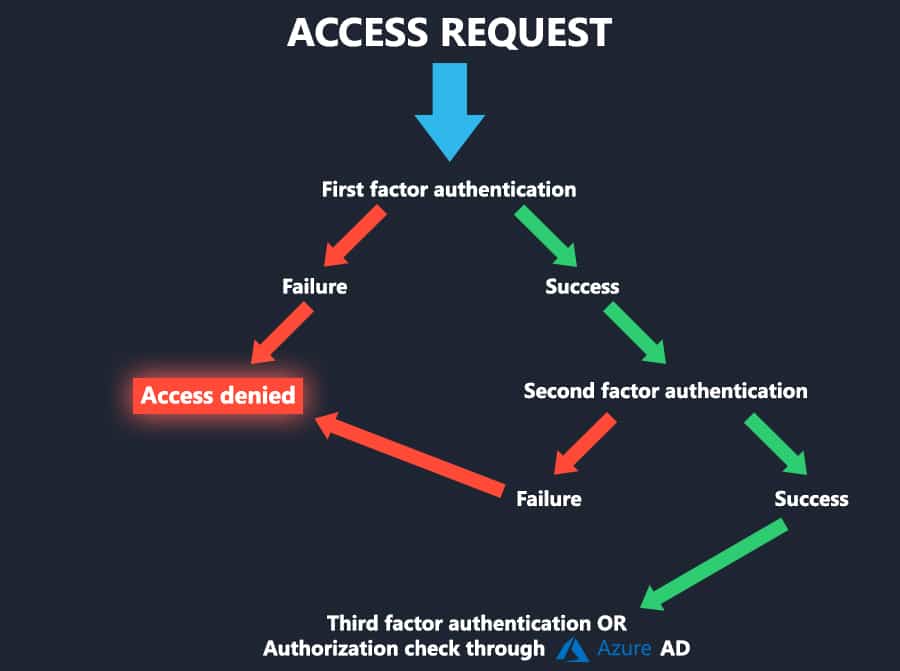
Ideally, the global admin would enforce MFA for all users. But the most important aspect comes next: setting up your conditional access policies through Azure AD.
Microsoft Azure AD has a default security setup that you can enable before making more granular changes.
Make sure to refer to our guide on access controls to see the kinds of actions you can restrict once users authenticate successfully.
Next Perimeter can help you set up your MFA and access controls within Microsoft 365 or Google Workspace. We can proactively manage your cybersecurity all for less than the price of one IT hire.
Give us a call today at 888-286-4816 or schedule a call today.