Every business that processes card transactions across the five major card brands must be PCI DSS Compliant.
Learn more about how to become and sustain PCI compliance to protect your customers’ sensitive data and your brand from a data breach or violation.
Introduction to PCI Compliance
Business. Customers. Trust. Success. Security. These are the building blocks of a growing business. If you remove security, you might just find yourself without customers and a business.
Business success is built on trust – if you are B2B, customers trust that your team is going to deliver on time and fulfill your contractual obligations.
If you are a business-to-consumer (B2C) company, your guests demand a highly personalized experience from start to finish while treating their personal and sensitive information with the utmost security.
If your organization experiences a data breach that compromises cardholder data, you might find out just how important information security and maintaining PCI compliance is to your business’s ability to thrive in today’s market.
New advances in eCommerce and payment technology required new standards and regulations to protect businesses and consumers.
Enter the Payment Card Industry Data Security Standard (PCI DSS), a standard put forth by the five largest credit card companies to help reduce costly consumer and data breaches.
Understanding and navigating PCI DSS compliance can feel overwhelming for business owners.
In this guide, we cover everything you need to know about PCI DSS compliance and walk you through best practices to safeguard your business and customers.
History of PCI Compliance
The internet gold rush of the late 1990s and early 2000s created adventurous merchants who wanted to leverage the internet for eCommerce.
As acceptance of online payments gained ground, so too came the risks. Online payments caught the eye of malicious individuals.
Soon cybercriminals began compromising card processing systems, e-retailers, and payment networks to extract cardholders’ information to purchase prepaid cards, gift cards, and goods online or resale.
With major credit card companies facing skyrocketing rates of fraud and backlash from consumers Visa, MasterCard, American Express, Discover, and JCB came together to create a comprehensive standard for all merchants in the payment cycle, on December 15, 2001, PCI DSS Version 1.0 was released.
As the internet era began to reach maturity with online payments garnering mainstream adoption, more businesses brought their payment processing systems online.
Many companies began connecting virtual and physical terminals wirelessly and interconnecting multiple locations to establish centralized databases.
Today, businesses collect vast quantities of personal information to create more connected and personalized experiences for customers.
These brand-new opportunities of commerce subjected businesses as well as consumers to more risks – and the opportunity for scammers to take charge card details from compromised networks.
To help with managing compliance standards, the payment brand names also established the PCI Security Standards Council as an independent body, with a set mission to “monitor threats and improve the industry’s means of dealing with them, through enhancements to PCI Security Standards and by the training of security professionals.”
The PCI Security Standards Council is led by a policy-setting Executive Committee, composed of representatives from the five founding global payment brands and Strategic Members.
A Board of Advisors, drawn from Participating Organizations, provides input to the organization and feedback on the evolution of the PCI Standards.
It’s key to note that the PCI Security Standards Council is responsible for setting the standards and requirements that sellers must adhere to – such as self-assessment questionnaires, security checklists, and PCI-compliant applications, it’s the responsibility of the card brands to enforce PSI DSS compliance criteria among sellers and organizations that accept credit cards.
What Is PCI DSS Compliance?
The Payment Card Industry Data Security Standard (PCI DSS) was developed by the five major credit card companies American Express, Discover, JCB, Master Card, and VISA.
PCI DSS was meant to enhance cardholder data security and facilitate the broad adoption of consistent data security measures globally to mitigate risks involved through online purchases or transactions while preventing data loss and security breaches.
PCI DSS provides a baseline of technical and operational requirements designed to protect account data. These measures apply to all entities involved in payment card processing—including merchants, processors, acquirers, issuers, and service providers.
PCI DSS also applies to all other entities that store, process, or transmit cardholder data (CHD) and/or sensitive authentication data (SAD).
While PCI DSS has no legal authority to compel compliance, it is a requirement of any business that wishes to facilitate transactions from any of the major card associations.
Who does PCI Compliance Apply to?
PCI Compliance applies to any business that accepts credit or debit card transactions from any of the five major card associations (brands), including American Express, Discover, JCB, MasterCard, or Visa.
PCI DSS Compliance also applies to service providers (discussed below), any business entity that is not a payment brand (e.g. Visa), directly involved in the processing, storage, or transmission of cardholder data.
For example, a managed IT service provides that provides managed firewalls or security solutions to a merchant or business accepting card payments is considered a ‘service provider’ and is co-responsible for maintaining PCI compliance.
PCI Compliance Requirements
PCI DSS comprises a minimum set of requirements for protecting account data and may be enhanced by additional controls and practices to further mitigate risks, as well as local, regional, and sector laws and regulations.
Additionally, legislation or regulatory requirements may require specific protection of personal information or other data elements (for example, cardholder name).
PCI DSS does not supersede local or regional laws, government regulations, or other legal requirements.
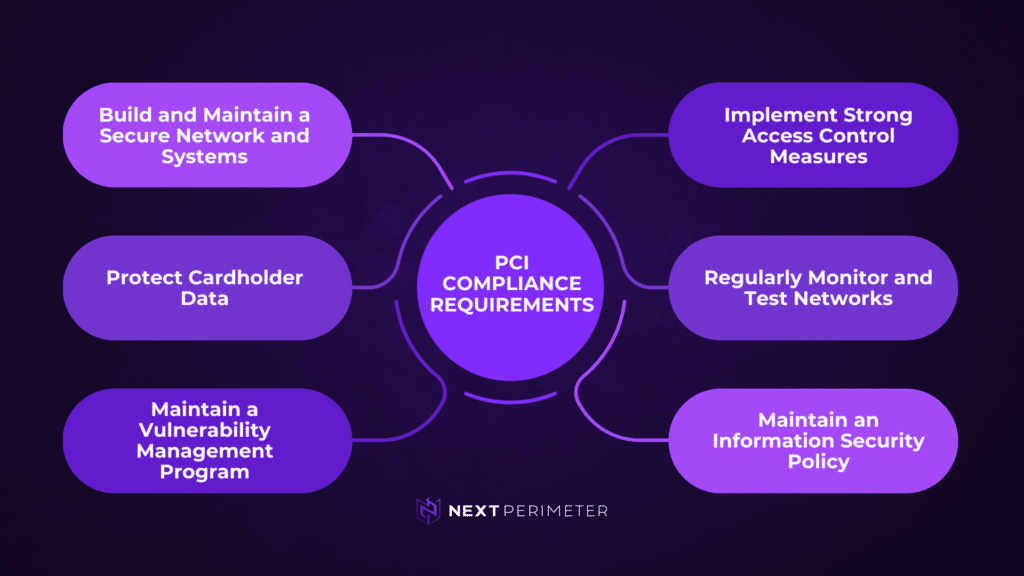
The PCI Data Security Standard (PCI DSS) is the global security standard for all merchants and retailers.
This standard is based on 12 requirements from 6 goal categories and all must be met to achieve compliance. These requirements are as follows:
| Goals | PCI DSS Compliance Requirements |
|---|---|
| Build and Maintain a Secure Network and Systems |
|
| Protect Cardholder Data |
|
| Maintain a Vulnerability Management Program |
|
| Implement Strong Access Control Measures |
|
| Regularly Monitor and Test Networks |
|
| Maintain an Information Security Policy |
|
How Does The PCI Security Standards Council Define Account Data?
PCI DSS applies to all entities involved in payment card processing—including merchants, processors, acquirers, issuers, and service providers.
PCI DSS also applies to all other entities that store, process, or transmit cardholder data and/or sensitive authentication data. Cardholder data and sensitive authentication data are defined as follows:
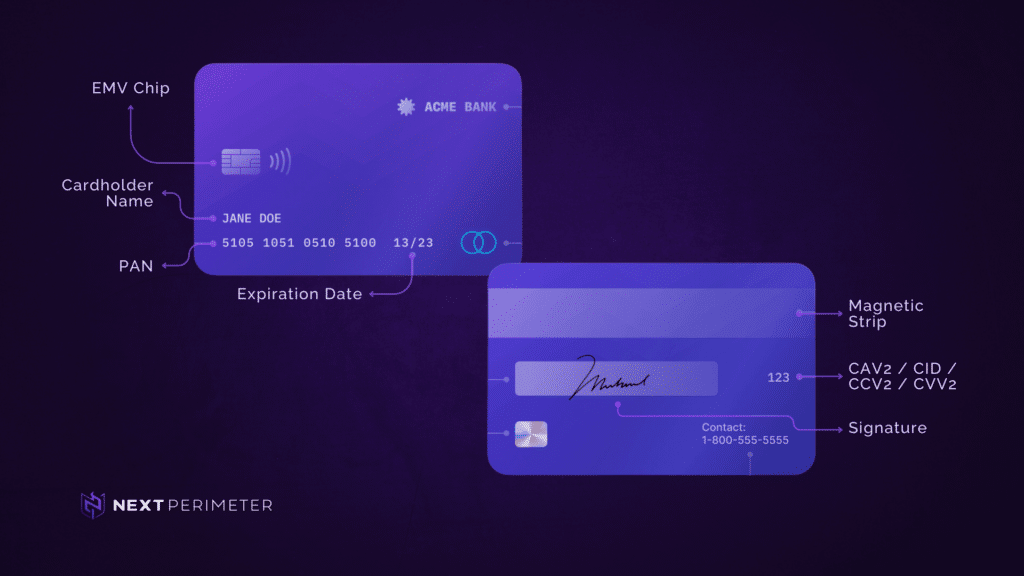
| Cardholder Data | Sensitive Authentication Data |
|---|---|
|
THIS DATA CANNOT BE STORED PER PCS DSS 3.2
|
Business Protection. Redefined.
The primary account number is the defining factor for cardholder data. If cardholder name, service code, and/or expiration date are stored, processed, or transmitted with the PAN, or are otherwise present in the cardholder data environment (CDE), they must be protected in accordance with applicable PCI DSS requirements.
PCI Compliance Levels
If you accept card payments with any one of the five PCI DSS card brands (American Express, Discover, JCB International, MasterCard, and Visa), then your company is required to be PCI DSS compliant.
Each merchant is categorized in one of four levels (Level 1 – Level 4) based on the number of transactions processed across all channels and whether or not your company has experienced a cyberattack that compromised cardholder account data.
Merchants with higher volumes of transactions are held to more stringent compliance standards than their lower volume counterparts because of the inherent risks.
For example, Level 4 merchants processing 6 Million or more transactions are required to work with Internal Security Assessors (ISAs), Qualified Security Assessors (QSAs), and PCI Council Approved Scan Vendors (ASVs) to maintain their PCI DSS compliance status.
Every seller falls into one of the four categories depending on their transaction volume during a 12-month period. While each credit card brand has its own slightly different criteria, generally the PCI-compliance levels are as follows*:
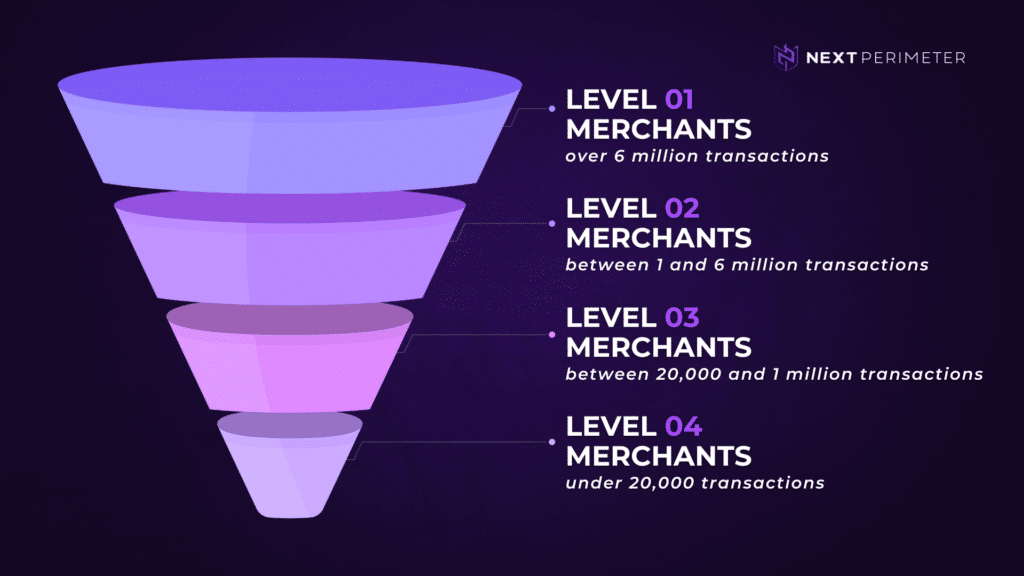
Level 1 Merchants
Level 1 is the highest level of PCI compliance of the four merchant levels. Merchants that process over 6 million transactions per year whether card present, card not present, online, or in-store, are considered a Level 1 Merchant.
In addition, any merchant that has had a data breach or successful cyberattack (internal or external) that resulted in compromised payment card information is automatically elevated to Level 1.
It’s important to note that card associations can enhance the compliance level of a merchant at their discretion. Here are the requirements for Level 1 merchants to sustain PCI compliance:
- File an Annual Report on Compliance (ROC) by a Qualified Security Assessor (QSA) or Internal Auditor if signed by an officer of the company. It’s highly recommended by the PCI Council for the Internal Auditor to obtain a PCI SSC Internal Security Assessor (“ISA”) certification.
- Submit an Attestation of Compliance (AOC) form
- Conduct quarterly network scans by an Approved Scan Vendor (ASV)
Level 2 Merchants
Merchants that process one to six million transactions across all channels annually are designated as Level 2 merchants. Level 2 merchants are required to complete the following to maintain PCI compliance:
• Complete a Self-Assessment Questionnaire (SAQ) annually– here’s a link to the PCI DSS SAQ version 3.2
• Submit an Attestation of Compliance (AOC) form (Word document link) each year
• Complete and obtain evidence of passing a vulnerability scan with an Approved Scanning Vendor (ASV)
• Conduct a quarterly network scan by an ASV
Level 3 Merchants
Any merchant with more than 20,000 combined transactions annually but less than or equal to one million total transactions across all channels is considered a Level 3 merchant. Level 3 merchants are required to:
- Complete a Self-Assessment Questionnaire (SAQ)
- Submit an Attestation of Compliance (AOC) form each year
- Complete and obtain evidence of passing a vulnerability scan with an Approved Scanning Vendor (ASV)
- Conduct a quarterly network scan by an ASV
Level 4 Merchants
Level 4 merchants include any seller that processes less than 20,000 payment transactions across all channels. Level 4 merchants are required to:
- Complete the Annual Self-Assessment Questionnaire (SAQ)
- Submit an Attestation of Compliance (AOC) form each year
- Conduct a quarterly network scan by an Approved Scan Vendor (ASV)
Service Providers and PCI DSS Compliance
A Service Provider is a business entity directly involved in the processing, storage, or transmission of cardholder data on behalf of another business.
This also includes companies that provide services that control or impact the security of cardholder data (e.g. Next Perimeter).
Service providers include companies that provide managed IT services, managed firewalls, intrusion detection software or services, and general security or infrastructure support for organizations that accept card payments.
Level 1 Service Provider
Level 1 Service Providers are service providers that store, process, or transmit more than 300,000 credit card transactions annually.
PCI Requirements:
- Annual Report on Compliance (ROC) by a Qualified Security Assessor (QSA)
- Quarterly network scan by an Approved Scanning Vendor (ASV)
- Penetration Test
- Internal Scan
- Bi-annual network segmentation tests
- Attestation of Compliance (AOC) Form
Level 2 Service Provider
These are service providers that store, process, or transmit less than 300,000 credit card transactions annually.
PCI Requirements:
- Annual Self-Assessment Questionnaire (SAQ)
- Quarterly network scan by an ASV
- Penetration Test
- Internal Scan
- Bi-annual network segmentation tests
- AOC Form
Note: In some cases, a Level 2 Service Provider will be asked by its partners, clients, or integration partners to validate compliance as a Level 1 with a QSA onsite assessment. Level 2 Service Providers will also sometimes choose to validate as a Level 1 to be listed as one of Visa’s Global Registry of Approved Service Providers.
How To Become PCI Compliant
The first step a business must take to become PCI compliant is to shift its belief that obtaining and sustaining PCI DSS compliance is difficult to achieve.
Many business owners become intimidated after their initial research or perceive that achieving PCI DSS compliance is more expensive and difficult than it actually is.
While, yes, the process can be complex – businesses mustn’t procrastinate or slack on shoring up PCI DSS compliance policies, payment data management procedures, and/or avoid taking a proactive approach to cybersecurity.
Secondly, business executives and stakeholders need to stop thinking about PCI Compliance solely in terms of ‘meeting compliance’ and instead translate ‘meeting compliance’ to ‘implementing and maintaining a strong physical, data, and cybersecurity posture.
The vast majority of PCI compliance penalties are levied as the result of a data breach that occurred because the organization refused to implement foundational security best practices or did not have active threat monitoring, detection, and remediation strategies.
Being PCI compliant involves implementing security controls outlined in the PCI DSS, signing a contract agreeing to a payment brand or merchant acquirer’s terms for PCI compliance, and completing an annual self-assessment.
These are the five (simplified) steps a business will need to take to become PCI compliant:
1. Analyze Your Merchant Compliance Level
The first step once you’re ready to begin the journey of PCI compliance is to review the four merchant levels (discussed above) to identify what your PCI requirements or action items are to complete.
There are different security standards based on what banks you work with and how many transactions you hand. Also, whether or not your business has been a victim of a data breach that compromised cardholder data.
Different companies have different standards here—for example, here are MasterCard’s, and Visa’s criteria, which describe four and five levels of businesses, respectively. Analyze where you fall, and how your business is described in PCI’s general standards so you’re ready for the next steps.
2. Complete a Self-Assessment Questionnaire (SAQ)
The self-assessment questionnaire (SAQ) is a relatively painless guidebook you can use to assess your current compliance level. There are actually nine different versions of the SAQ guidebook, but don’t let that intimidate you.
These versions are available for different business types, so you’ll only need the book that applies to your business. When you have it, the guidebook will walk you through about a dozen different requirements, and for each, you’ll answer “yes,” “no,” or “N/A.”
This will help you identify the missing pieces of your company’s payment security. Most businesses will fall between Merchant Levels 2 – 4, the requirements are relatively the same across these levels:
- Complete a Self-Assessment Questionnaire (SAQ)
- Submit an Attestation of Compliance (AOC) form each year
- Complete and obtain evidence of passing a vulnerability scan with an Approved Scanning Vendor (ASV)
- Conduct a quarterly network scan by an ASV
3. Now That You’ve Completed Your ASV – It Might Be Time to Remediate
You’ve completed your Self-Assessment Question (SAQ) and done your due diligence in researching PCI standards.
Your business is now ready to obtain and provide evidence of passing a vulnerability scan by an Approved Scanning Vendor. If this is your first time completing an ASV, you might find that you have a few items to remediate.
Work with your IT team to correct any security vulnerabilities, hardware upgrades, or documentation required to bring your business into full compliance.
We’ve created a 9-Step Approach to Creating an Effective PCI Compliance Remediation Plan plan below to help you get started.
Once you’ve made the necessary changes, it’s time to have the ASV rescan and document proof that your organization passed. If remediation was required, take a moment and review your SAQ for accuracy and update as needed.
4. Complete a formal attestation of compliance.
Once you’ve made any changes necessary and have updated your SAQ, you can fill out a formal attestation of compliance (AOC).
This is a formality that claims your business is fully compliant with all relevant PCI standards—and again, there are nine different types based on the nature and size of your business.
Once you’re done with that, you can have a qualified security assessor review your work and create a report on your compliance to validate your own findings.
5. File the paperwork.
Congratulations – the long hours of research, determination (and possibly some dread), and money spent has paid off.
Your business is ready to package up all the paperwork and deliver it to the card associations or banks you process payments with.
You’ll need to submit your SAQ, AOC, proof that you passed your ASV, and any other documentation requested.
Understanding the Cost of PCI Compliance: What to Expect
If your business is required to be PCI compliant, one of the first questions you may ask is: How much will this cost?
The answer isn’t straightforward, as compliance costs vary based on your current infrastructure, security measures, and business needs. Below, we break down the key factors that determine the cost of PCI compliance and how you can optimize expenses while maintaining security.
What Impacts the Cost of PCI Compliance?
1. Your Network Setup
If your network is already structured with security best practices in mind, achieving PCI compliance may only require minor fixes—such as running internal and external scans, securing an SSL certificate, or closing open ports.
However, if your network lacks segmentation or has outdated hardware, compliance can be more complex and costly. For example, you may need to:
- Upgrade to business-class firewalls and routers for proper network segmentation
- Implement end-to-end encryption for communication platforms and remote access
- Replace outdated systems that fail to meet security standards
2. Security Measures in Place
Businesses that lag in security often face additional expenses. Key considerations include:
- Are your communication platforms encrypted?
- Do you have secure remote access? (e.g., using a VPN instead of open ports like 3389)
- Do you utilize File Integrity Monitoring (FIM)?
- Have you implemented tokenization, credit card vaulting, or Point-to-Point Encryption (P2PE)?
If any of these areas are lacking, your business may require additional security solutions to meet PCI requirements.
3. IT Resources and Support
The level of in-house IT support you have significantly affects costs. Ask yourself:
- Do you have a dedicated IT professional or team?
- Are you working with a Managed IT Service Provider?
- Is your IT environment well-documented with a complete inventory of all connections to cardholder data?
Businesses with internal IT teams may be able to handle compliance independently, while those without IT expertise may need to invest in external consulting or managed security services.
4. PCI Scope and Documentation
Determining the scope of your cardholder data environment (CDE) is crucial. Many businesses mistakenly over-scope their PCI environment, leading to wasted resources. By accurately defining your PCI scope, you can:
- Reduce compliance costs by limiting the number of systems in scope
- Simplify security controls and ongoing monitoring
- Avoid unnecessary upgrades and security implementations
5. Patch Management & Security Best Practices
A well-maintained IT infrastructure reduces compliance costs over time. Having a formal patch management strategy ensures timely updates and reduces vulnerabilities that could otherwise result in expensive security fixes.
How to Minimize PCI Compliance Costs
- Optimize Your Network Setup: Ensure that your firewalls, routers, and network segmentation are configured properly from the start.
- Use the Right Security Tools: Implement VPNs, encryption solutions, and tokenization to reduce compliance scope.
- Leverage a Managed IT Service Provider: If you don’t have internal IT support, outsourcing compliance to an expert can be more cost-effective than in-house solutions.
- Accurately Define PCI Scope: Avoid over-scoping your CDE to prevent unnecessary security costs and operational complexity.
- Stay Proactive with Compliance & Security Practices: Implement security best practices early on to reduce long-term remediation costs.
Get a Custom PCI Compliance Cost Estimate
As every business has unique IT infrastructure and security needs, the cost of PCI compliance is highly variable.
Want to know your exact PCI compliance costs? Contact Next Perimeter for a network assessment. We’ve helped hundreds of businesses secure their networks, strengthen security controls, and implement processes to achieve and maintain PCI compliance efficiently.
How Long Does It Take to Bring a Business Into Full PCI Dss Compliance?
In our experience, most networks that were configured correctly from the start will only require a day’s work to bring the business into compliance.
Of course, there’s training that must be done with relevant personnel so that everyone understands PCI compliance and your now well-optimized strategy to sustain PCI DSS compliance.
However, from a technological perspective, minimal work is usually required if your IT environment is up-to-par.
By properly configuring your network and operating using IT best practices, you can avoid time-consuming PCI compliance remediation efforts down the line.
16 Best Practices to Achieve and Maintain PCI Compliance
Ensuring 100% PCI compliance is not just about meeting regulations—it’s about protecting your business and customers from potential security threats. To help you sustain compliance and create a secure culture within your organization, here are 16 best practices your team should follow.
1. Perform Scans Early and Regularly
Quarterly scans are required for PCI compliance and must be conducted by an Approved Scanning Vendor (ASV). Early scans allow time to identify vulnerabilities and remediate them before submission. A proactive approach prevents last-minute issues and avoids operational bottlenecks.
2. Encrypt Stored Cardholder Data
PCI DSS Requirement 3 mandates that all Primary Account Number (PAN) data must be rendered unreadable through encryption. Ensure encryption is applied to all storage locations, including databases, backups, logs, and even physical records.
3. Use Network Segmentation and Test It Annually
Network segmentation isolates cardholder data environments (CDEs), reducing PCI scope and compliance costs. PCI DSS requires merchants to test segmentation annually and service providers to do so bi-annually.
4. Secure Cardholder Data in Transit
PCI DSS Requirement 4 requires encryption of data in transit using secure transport protocols and AES-128 bit encryption. Avoid transmitting unprotected PANs through email or chat applications. Secure collaboration tools, like Microsoft Office 365 Message Encryption, can help businesses communicate safely.
5. Be Proactive, Not Reactive
Many businesses handle compliance reactively, diverting resources from revenue-generating tasks. A proactive compliance strategy improves security posture, reduces financial risks, and enhances monitoring across all communication channels.
6. Train Employees in Security Awareness
Employees are often the weakest security link. Regular PCI compliance training should be mandatory for all staff handling sensitive data. Ensure they understand security policies, phishing threats, and data protection best practices.
7. Prepare for QSA Assessments
Understanding where cardholder data is stored and transmitted is crucial. A comprehensive network diagram helps map out all data flow points. Reducing PCI scope by eliminating unnecessary PAN storage simplifies compliance efforts.
8. Partner with PCI-Compliant Payment Providers
Choose PCI Level 1 service providers, which meet the highest compliance standards, including bi-annual penetration testing and strict reporting requirements.
9. Restrict Access and Prevent PCI Scope Creep
Limit access to cardholder data to only necessary employees. Implement unique ID credentials and track actions on credit card information using Access Rights Management (ARM) software. Microsoft Azure Rights Management provides a robust solution for access control.
10. Be Cautious with Open-Source eCommerce Platforms
WooCommerce, while powerful, requires additional security configurations to be PCI-compliant. Use SSL for checkout pages and restrict unnecessary access to payment data.
11. Implement a Web Application Firewall (WAF)
A WAF protects against malicious traffic and web-based attacks. PCI DSS Requirement 6.6 mandates that your WAF be updated regularly, generate audit logs, and block or alert on suspicious activity.
12. Develop a Patch Management Strategy
Patch management ensures software vulnerabilities are addressed before attackers exploit them. The average time to patch is 102 days—too long for security threats. Track updates in a structured system to reduce response times.
13. Define Security Metrics and KPIs
Monitor your IT environment with key metrics such as system availability, maintenance efficiency, and average time to patch. Consistently tracking these KPIs helps optimize compliance and security strategies.
14. Monitor Third-Party Service Providers
Vendors processing, storing, or transmitting cardholder data must comply with PCI standards. Regularly audit third-party compliance to minimize security risks and avoid potential breaches.
15. Maintain Detailed Documentation and Logs
PCI DSS Requirement 12 mandates keeping records of security policies, risk assessments, and compliance measures. Requirement 10 focuses on log monitoring, ensuring security events and critical system activity are tracked and stored securely.
16. Evolve Compliance Programs with Changing Threats
Cyber threats constantly evolve. Stay ahead by adapting security policies, monitoring trends, and working with Managed IT Service Providers to ensure your cardholder data remains protected.
Final Thoughts
Achieving PCI compliance is an ongoing process that requires commitment, collaboration, and proactive measures. By following these best practices, your business can maintain a strong security posture, minimize risk, and confidently meet PCI DSS requirements.
Need help securing your business? Work with certified PCI DSS compliance experts like Next Perimeter to strengthen your security and compliance efforts.
(Source: PCI Security Standards Council – Best Practices for Maintaining PCI DSS Compliance)
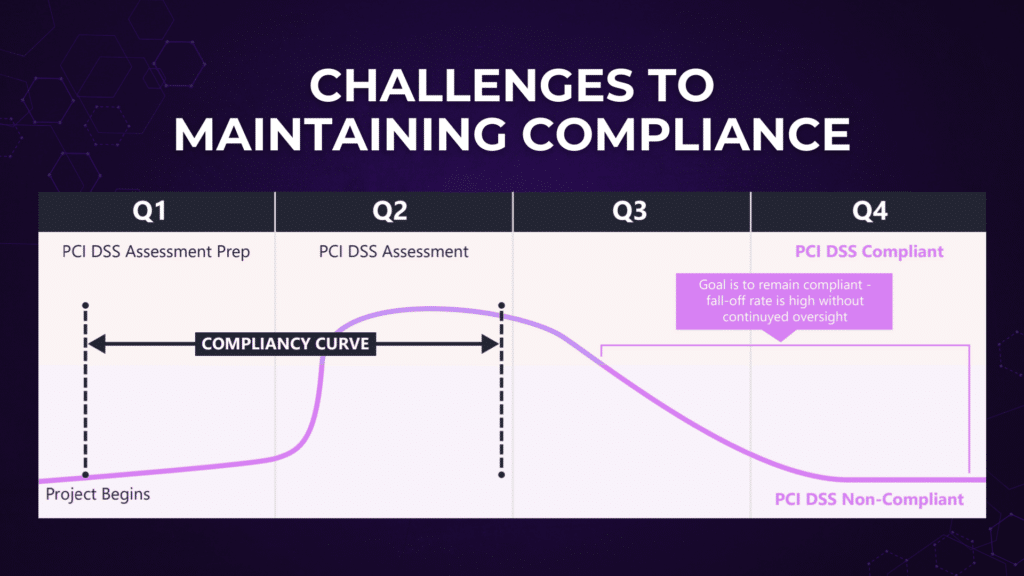
Challenges to Maintaining Compliance
Organizations are struggling to maintain PCI DSS compliance.
According to a PCI Security Council report released in January, more than 44 percent of companies see the effectiveness of the PCI DSS controls and overall compliance decline after a PCI assessment is completed.
This correlates with the three percent compliance decline seen for the first time since Verizon started tracking PCI compliance in 2012.
While the cause for declining compliance is myriad the PCI Security Council outlines five common reasons that businesses begin dropping out of PCI compliance:
- The digital age and technology continue to evolve at breakneck speeds. Pressures to adapt to ever-increasing customer demands and emerging technologies and the resulting changes to an organization’s business goals, structure, and technology infrastructure.
- Organizational complacency, assuming what was good enough last year will be good enough in future
- Overconfidence in organizational practices, resulting in a lack of resources devoted to regular monitoring, detection, tracking, or an effective employee training program can push businesses out of compliance.
- Inability to assign the right people, tools, and processes, and lack of executive leadership commitment to maintaining data security.
- Failure to accurately scope the organization’s cardholder data environment (CDE) as business practices evolve with the introduction of new products or services, or
Businesses that focus solely on annual PCI DSS assessments to validate the quality of their cardholder data security programs are missing the intent of PCI DSS to enhance cardholder data security, and likely see their PCI DSS compliance state “fall off” between assessments.
To maintain a consistent level of security and compliance, organizations should focus on implementing an effective physical and digital security posture with integrated security monitoring, threat detection, and prevention systems that work cohesively to secure the IT environment as a whole instead of solely on “meeting compliance.”
How Much Could Failing PCI Compliance Cost Your Business?
According to Verizon’s Payment Security Report 47.5% of businesses assessed did not meet full compliance.
If your business does not comply with PCI standards, you could be at risk for data breaches, fines, card replacement costs, costly forensic audits and investigations into your business, brand reputation damage, and more.
Standard fines and penalties imposed by Payment Card Brands for card data breaches take into consideration the following:
- Number of card numbers stolen
- Circumstances surrounding the incident
- Whether track data was stored or not
- Timeliness of reporting incident
Although PCI compliance is not a law but rather a set of standards established and regulated by the major card brands, if your business is not compliant you might expect any one or all of the following scenarios:
- PCI non-compliance fee: Most payment processing companies will charge a PCI non-compliance fee if your business does not fulfill all the PCI DSS requirements, such as not submitting the annual Report on Compliance (ROP) or Self-Assessment Questionnaire (SAQ), Attestation of Compliance (AOC), or proof that you’ve passed your vulnerability scans completed by an Approved Network Scan (ANS) service provider.Non-compliance fees are largely dependent on your Merchant Service Provider’s terms and conditions but can range from $10 – $45 (or more) for each month out of compliance. The card brand can also levy fines which we discuss below.
- PCI non-compliance fine: If a security breach occurs, and consumer credit card data is leaked or compromised AND your records indicate non-compliance; you might end up being fined $5,000 to $100,000 per month by the credit card associations.
- PCI fines for storing sensitive authentication data: up to $100,000 per month. Sensitive authentication data includes full track data (magnetic-stripe data or equivalent on an EMV chip), CAV2/CVC2/CVV2/CID, PINs, and PIN blocks.
- PCI non-compliance & revocation: If non-compliance persists and/or credit card data is compromised due to a sheer amount of negligence or sloppy IT infrastructure, your acquiring bank may revoke your ability to accept credit cards, and place you on a merchant account blacklist (Match List – see below) which could effectively end your ability to do business.
Other financial implications in the event of a data breach affecting card data:
- Fines levied by card associations to make notifications to all cardholders and replace credit cards
- Costs of notifying taxpayers of an incident, as directed by the Identity Theft Protection Act
- Forensic Investigation Costs
- The cost associated with discontinuing accepting cards
- The cost of an annual on-site security compliance audit is estimated at $20,000 every year
- Business reputational damage – probably the most significant side effect of a data breach is the loss of trust by consumers.If your customers cannot trust your business to keep their data safe, you might find that they simply switch brands or take their hard-earned money to one of your competitors.According to Verizon’s Data Breach Report, 69 percent of consumers would be less inclined to do business with a breached organization.
What is the Terminated Merchant File or Mastercard MATCH List?
Merchant accounts (read businesses) that partake in fraudulent practices, receive excessive chargebacks or consumer complaints, or unintentionally facilitated, by any means, the unauthorized disclosure or use of account information may find themselves on the Terminated Merchant File (TMF) or MATCH (Member Alert to Control High Risk Merchants) List.
MATCH is a system created and managed by Mastercard which essentially is a ‘merchant blacklist’ database that contains information about businesses (and their owners) whose credit card processing privileges have been terminated.
The MATCH list not only affects the principal business owner – when a business is placed on the MATCH list, the business name, principal, and any business partners are recorded on this blacklist.
If you end up on this blacklist, you might find it extremely difficult to obtain a new merchant account from any other bank.
If you can find a merchant service provider that is willing to work with a business on the MATCH list, you will likely experience higher interchange rates and additional fees to mitigate the risks associated with your lack of compliance or less-than-ideal past business practices.
While the MATCH list uses codes to categorize the conditions and practices that resulted in a merchant being added to the MATCH list, it is a system largely without any checks and balances.
MasterCard’s own words clearly state that they do not verify or confirm the accuracy of the information reported, from section 11.1 of their MATCH Overview:
“MasterCard does not verify, otherwise confirm, or ask for confirmation of either the basis for or accuracy of any information that is reported to or listed in MATCH. It is possible that information has been wrongfully reported or inaccurately reported. It is also possible that facts and circumstances giving rise to a MATCH report may be subject to interpretation and dispute.”
The best way to prevent find yourself on the MATCH list is to ensure that your business is PCI compliant, adheres to cybersecurity best practices, follow your card brand’s terms of service, and avoid any risky transactions or unethical business practices.
Review the table below to understanding how merchants are categorized on MasterCard’s MATCH List:
“MasterCard does not verify, otherwise confirm, or ask for confirmation of either the basis for or accuracy of any information that is reported to or listed in MATCH. It is possible that information has been wrongfully reported or inaccurately reported. It is also possible that facts and circumstances giving rise to a MATCH report may be subject to interpretation and dispute.”
The best way to prevent find yourself on the MATCH list is to ensure that your business is PCI compliant, adheres to cybersecurity best practices, follow your card brand’s terms of service, and avoid any risky transactions or unethical business practices.
| MATCH List Reason Code | Title | Explanation |
|---|---|---|
| 1 | Account Data Compromise | Account data is stolen from the card-present merchant and used with other merchants |
| 2 | Common Point of Purchase | Account data is stolen from the card-present merchant and used with other merchants |
| 3 | Laundering | The merchant processed transactions that did not involve a bona fide cardholder |
| 4 | Excessive Chargebacks | The merchant breached predetermined chargeback thresholds |
| 5 | Excessive Fraud | The merchant breached predetermined fraud-to-sales dollar volume thresholds |
| 6 | MasterCard Questionable Merchant Audit Program | The merchant is labeled a “Questionable Merchant,” as determined by MasterCard guidelines |
| 7 | Bankruptcy, Liquidation, Insolvency | The merchant is unable to discharge all financial obligations |
| 8 | Violation of Standards | The merchant violated one or more of the card network’s regulations |
| 9 | Merchant Collusion | The merchant participated in fraudulent collusive activities |
| 10 | PCI DSS Noncompliance | The merchant wasn’t compliant with PCI DSS requirements |
| 11 | Illegal Transactions | The merchant processed illegal transactions |
| 12 | Identity Theft | The business owner’s identity is in question |
PCI DSS Compliance Remediation
A readiness assessment from a Qualified Security Assessor (QSA) will likely uncover gaps in PCI compliance that will need to be addressed before a formal PCI review.
If a QSA identifies compliance issues during the readiness assessment, you may be able to address some of those issues by reviewing and minimizing your scope of compliance, but existing issues will have to be properly remediated to comply with PCI DSS standards.
After the QSA conducts a readiness assessment, you can expect the assessor will work with your business to:
- identify and explain any existing gaps in compliance;
- develop a remediation plan, including technical fixes and policy and procedural updates; and
- recommend tools or third parties that can help complete the necessary technical and policy work.
It’s important to note that the PCI Security Standards Council has implemented controls to prevent a conflict of interest, due to strict requirements regarding “separation of duties”, a QSA cannot conduct remediation efforts identified during a readiness assessment.
A QSA can, however, recommend a third party to assist in the remediation and fill gaps identified by the QSA.
Our 9-Step Approach to Creating an Effective PCI Compliance Remediation Plan
Ensuring PCI compliance requires a structured and proactive approach. Follow these nine steps to create an effective PCI compliance remediation plan that safeguards your business while maintaining regulatory standards.
1. Plan Ahead
PCI remediation can be a lengthy and complex process. Once compliance gaps are identified, outline a detailed and workable remediation strategy from the beginning. Establish clear objectives, set expectations, and ensure all stakeholders are aligned before starting the process.
2. Get Organized
Structure your remediation efforts into two primary categories:
- Technical Remediation: Updating server configurations, installing firewalls, patching vulnerabilities, securing networks.
- Policy & Procedural Remediation: Creating new security policies, updating compliance documentation, employee training, and risk management.
A well-organized plan will save time, reduce costs, and minimize frustration for your team.
3. Assign Responsibilities
Clearly define roles and responsibilities for each remediation task. Identify the teams and key stakeholders accountable for implementing the necessary security controls and compliance measures. If needed, consider involving external Managed Service Providers (MSPs) specializing in PCI compliance.
4. Review Remediation Tools and Services
Leverage available resources to streamline compliance efforts:
- Work with your Qualified Security Assessor (QSA) to identify cost-effective, open-source compliance tools.
- Use industry-specific security templates to expedite remediation.
- Consider outsourcing security initiatives to specialists to enhance protection in an evolving threat landscape.
5. Budget Wisely
Although achieving PCI compliance requires an investment, the cost of non-compliance—including fines, data breaches, and reputational damage—is significantly higher.
Factor in potential costs such as:
- New POS hardware
- Upgrading servers and security software
- Purchasing additional user licenses
- Partnering with an IT security firm or third-party service providers
Careful financial planning will help prevent scope creep and unexpected expenses.
6. Set and Execute the Remediation Plan
Establish a clear timeline for your remediation efforts. Key tasks include:
- Strengthening network security
- Encrypting sensitive data
- Updating security documentation
- Implementing necessary PCI controls
Ensure all remediation actions align with PCI DSS requirements before moving to the testing phase.
7. Test and Verify
Before undergoing a formal PCI review, conduct thorough internal testing to confirm that:
- Security controls are properly implemented
- Policies and procedures are correctly followed
- Compliance gaps have been effectively addressed
Testing helps identify and resolve any remaining issues before your QSA assessment.
8. Conduct a Formal PCI Review
Once all remediation measures are in place, contact your QSA for an official PCI review. If all recommendations from the readiness assessment have been properly addressed, this process should confirm your PCI compliance status.
9. Maintain PCI Compliance
Achieving PCI compliance is not a one-time task—it requires ongoing effort. To sustain compliance:
- Continuously monitor and update security measures
- Assign responsibility for regular compliance checks
- Conduct periodic security tests and audits
- Keep up with evolving PCI standards
By following these best practices, your organization can maintain PCI compliance while strengthening its overall security posture.
Need Expert Guidance? For specialized support in PCI remediation, work with experienced compliance professionals like Next Perimeter to streamline your compliance efforts and enhance security.
PCI Compliance in Hospitality – Are You Fully Compliant?
The hospitality industry heavily relies on personal data to enhance guest experiences, yet it remains a top target for cyberattacks, accounting for 40% of global data breaches (HTFP Journal). Despite these risks, only 38.5% of hospitality organizations achieve full PCI compliance (Verizon).
High-Profile Data Breaches in Hospitality
- Marriott/Starwood Breach: Exposed 500 million guest records, including passport numbers, loyalty data, and government personnel information.
- AutoClerk Data Leak: Left hotel reservations and military travel details unprotected in an open database, compromising customer privacy and national security.
Why Hospitality Businesses Struggle with PCI Compliance
- High Employee Turnover: Frequent staff changes create security risks.
- Third-Party Vendor Risks: Integrated booking/payment systems introduce vulnerabilities.
- Franchise & Chain Security Gaps: A weak link in one location can expose the entire network.
- Diverse IT Systems: Managing multiple platforms complicates security enforcement.
How Next Perimeter Helps Secure Hospitality Businesses
Next Perimeter partners with luxury resorts, boutique hotels, and large chains to:
- Identify vulnerabilities with comprehensive security assessments
- Provide custom PCI compliance consulting
- Implement advanced threat protection for guest data security
- Train employees to reduce security risks
Protect Your Guests & Your Business
Achieving PCI compliance is crucial for securing customer data and maintaining trust. Contact us for a security assessment and stay ahead of evolving threats.
PCI Compliance Key Terms and Definitions You Need to Know:
Understanding PCI compliance requires familiarity with key terms. Below are essential definitions to help navigate PCI DSS requirements effectively.
- Account Data – Any cardholder data and/or sensitive authentication data under PCI DSS.
- Approved Scanning Vendor (ASV) – A PCI SSC-approved company authorized to conduct external vulnerability scans.
- Attestation of Compliance (AOC) – An annual form that merchants and service providers complete to confirm PCI DSS assessment results. It may include a self-assessment questionnaire, network scans, compliance reports, and formal attestation.
- Cardholder Data Environment (CDE) – The systems, processes, and personnel involved in the transmission, processing, or storage of cardholder data.
- Merchant – Any entity that accepts credit card payments from brands such as Visa, MasterCard, American Express, Discover, and JCB.
- PCI DSS (Payment Card Industry Data Security Standard) – A global security standard for businesses handling credit card transactions to protect cardholder data.
- PCI SSC (Payment Card Industry Security Standards Council) – A global organization responsible for developing, enhancing, and enforcing PCI DSS to ensure account data security.
- Qualified Security Assessor (QSA) – A PCI SSC-certified professional or organization that performs on-site PCI DSS assessments.
- Self-Assessment Questionnaire (SAQ) – A PCI DSS reporting tool used by entities to document their self-assessment results.
- Service Provider – A business that is not a payment brand but handles processing, storage, or transmission of cardholder data on behalf of another entity. Examples include managed IT service providers, firewall management services, and security monitoring firms.
By understanding these key terms, businesses can better navigate PCI compliance and take the necessary steps to protect cardholder data effectively.