A modern backup strategy is essential in 2025—yet most teams still rely on outdated tools built for on-prem servers and office networks.
The way we work has changed. Teams are remote. SaaS is the norm. Devices roam. But most backup strategies still assume your data sits on a server, on a network, or in a cloud platform that magically handles retention.
It doesn’t.
At Next Perimeter, we see backup as more than insurance — it’s a non-negotiable layer of operational resilience, deeply integrated into how we manage identities, devices, and collaboration tools. It’s not a product. It’s a lifecycle responsibility. And in the SaaS era, it’s the difference between resilience and ransom.
Legacy Backup: Why It’s Failing Modern Teams
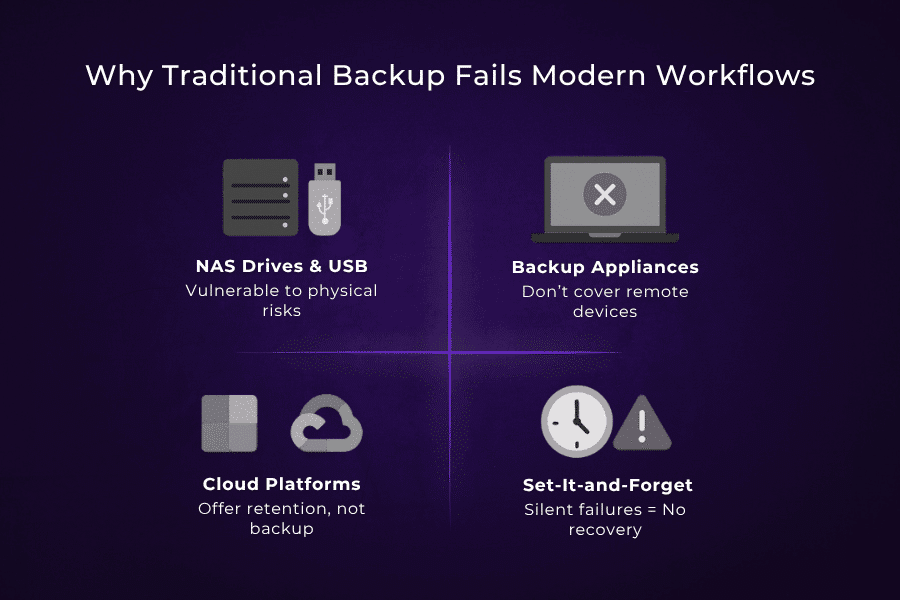
The tools that worked when everyone sat in the same office now introduce risk when data is everywhere. Here’s where traditional strategies fall apart:
- NAS drives and USB backups are still exposed to theft, fire, and ransomware.
- Backup appliances don’t help remote laptops or hybrid workers.
- Cloud platforms like Microsoft 365 and Google Workspace don’t include true backup — just limited retention.
- “Set-and-forget” tools often break silently, leaving teams unprotected.
The illusion of protection is worse than no protection at all. By the time something breaks, it’s too late to realize your backup strategy was based on assumptions that no longer apply.
Cloud ≠ Backup: The Most Dangerous Misunderstanding in IT
One of the most common — and dangerous — myths in modern IT is that Microsoft or Google “already back everything up.”
They don’t.
Deleted OneDrive files only last 30 days — and when a user is offboarded, their data can disappear permanently.
Shared Drives, Teams files, or group mailboxes can be deleted or overwritten with no rollback options unless a dedicated SaaS backup exists.
Microsoft 365 is designed for availability, not long-term recoverability. That’s your responsibility.
This gap in understanding has led to data loss, compliance failures, and expensive restoration efforts. With Next Perimeter, SaaS backups are enforced — not optional.
Modern Backup in a Zero Trust World
In a zero trust architecture, recovery isn’t a luxury — it’s a baseline. You assume breach and build for resilience.
Our backup strategy follows the data, not the legacy infrastructure. Here’s how we protect each layer:
- Endpoints
Our device blueprints ensure that OneDrive sync and known folder redirection (Desktop, Documents, Pictures) are configured on every managed machine. Intune and config.office.com monitor health and enforce compliance.
- Cloud Applications
We back up Microsoft 365 and Google Workspace accounts using NinjaOne’s integrated SaaS backup platform. Retention follows the user identity, not the device.
- Collaboration Spaces
SharePoint, Teams, and Shared Drives are included — so your team’s shared content isn’t a blind spot.
- Servers (if any)
For clients with LOB servers, backups are enforced by policy. The license is included; storage is billed based on usage. No exceptions.
This architecture supports every modern workplace model — from remote-first SaaS orgs to hybrid legal or finance teams.
Understanding RPO and RTO: The Two Questions You’ll Ask Too Late
Backup isn’t just about if you can recover — it’s about how much you lose and how long you’re down.
These are the two key metrics:
- RPO (Recovery Point Objective):
How much data can you afford to lose? If you only back up once per day, you might lose 23 hours of work.
- RTO (Recovery Time Objective):
How quickly do you need to be back online? Downtime impacts payroll, compliance, contracts — everything.
At Next Perimeter, we handle these variables on your behalf — mapping RPO/RTO to your real-world needs during onboarding or as part of your QBR. You don’t need to configure anything. You just need to tell us what’s critical.
What Is an Immutable Backup — and Why Ransomware Hates It
Immutability means once a backup is written, it cannot be changed — not even by admins. That matters, because modern ransomware often targets your backups first.
Immutable backups use object lock or WORM (Write Once, Read Many) policies to prevent tampering.
This creates a last line of defense — a snapshot of your data that malware can’t encrypt or delete.
While not every backup is immutable by default, we support it where warranted based on risk and compliance posture.
Bottom line: You don’t need immutability until you really need it. And by then, it’s too late to set it up.
Backups & Ransomware: Where Security and IT Converge
Backups and cybersecurity are deeply intertwined — but at Next Perimeter, we draw a clear operational line:
- Our IT team (Managed Services) owns monitoring, remediation, and all restoration requests.
- Our MXDR/SOC team only gets involved during active breach response, or when backup is needed to recover after an incident.
- Alerts are automatically ticketed via HaloPSA from NinjaOne’s monitoring. You’re never left wondering if backups are working.
This division of responsibilities keeps things simple, fast, and accountable — so you always know who’s on point.
Backup Is a Compliance Requirement, Not Just an IT Best Practice
If you’re subject to HIPAA, FINRA, SOC 2, or similar, backup isn’t optional — it’s an enforceable requirement.
Regulators expect to see retention policies, recovery procedures, and evidence of successful restores.
Many compliance failures occur not because backups are missing — but because they’re unverifiable.
At Next Perimeter, we can provide clients with the documentation and proof they need for audits, certifications, or incident response.
Backup is more than protection — it’s evidence.
Zero Trust Isn’t Just About Access — It’s About Recoverability
We talk a lot about device posture, MFA, SSO, and policy enforcement. But if your device is encrypted, stolen, or wiped — can you get that data back?
With Next Perimeter:
- New laptops are provisioned with OneDrive backup defaults at Day 1.
- Data is synced securely before the user ever logs in.
- If a device is lost or decommissioned, we can restore the identity and data to a new machine within hours — with zero disruption.
Backup is part of device hygiene — just like patching or EDR. We don’t treat it separately. It’s part of the blueprint.
Lifecycle-Backed Protection
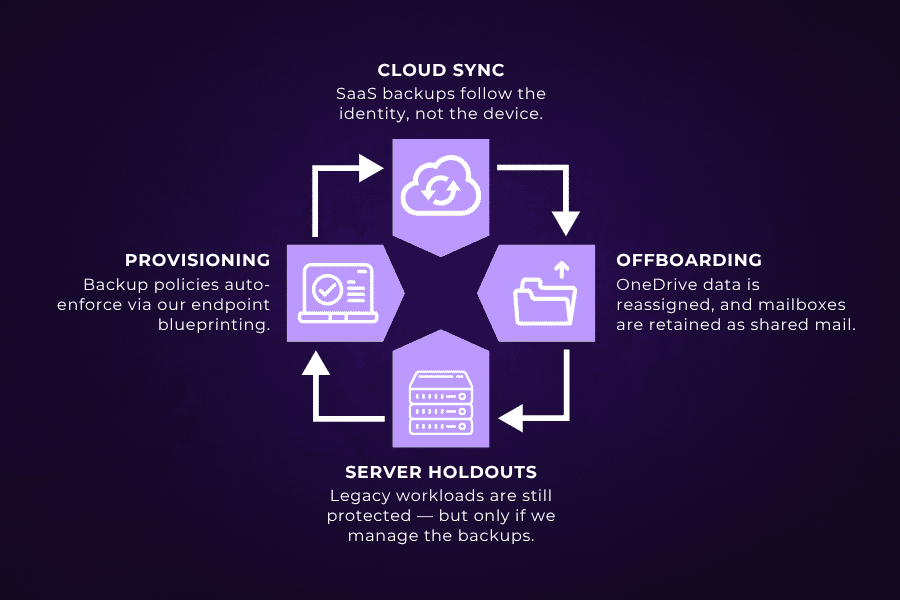
We back up every user by default — no special requests needed. It’s all part of the managed lifecycle:
- Provisioning
Backup policies auto-enforce via our endpoint blueprinting.
- Cloud Sync
SaaS backups follow the identity, not the device.
- Offboarding
OneDrive data is reassigned, and mailboxes are retained as shared mail.
- Server Holdouts
Legacy workloads are still protected — but only if we manage the backups.
No toggles. No add-ons. Just automatic protection, tied to each identity and asset we manage.
Visibility & Control: What Clients See
Even though we handle everything behind the scenes, we give you control when it matters:
- File- or mailbox-level restores available via ticket
- Unlimited retention while you’re an active client
- Offboarding protection ensures nothing slips through the cracks
- PERIMETER Score visibility for backup coverage is coming in 2025
We remove guesswork, not transparency.
Let’s Evaluate Your Backup Readiness
If your provider can’t show you what’s backed up, how long recovery will take, or what your RPO/RTO is — you’re overdue for a review.
We’ll help you assess:
- What’s backed up (and what’s not)
- SaaS and endpoint coverage
- Offboarding and retention readiness
- Legacy server exposure (if any)
- Compliance risks tied to data protection
In 2025, backup isn’t a checkbox — it’s your contingency plan.