You may have come across the term ransomware recently in the news, or perhaps you noticed people using the term ransomware more frequently. So what exactly is ransomware?
Ransomware is software used by hackers to block access and encrypt files on a computer system until a ransom is paid. Individuals, hospitals, schools, government agencies, police departments, and other relatively easy targets were among the first to experience the power of ransomware, but now hackers have their eyes set on much higher stakes. Cybercriminals are now using more sophisticated versions of ransomware to infect the computer systems of major institutions. For instance, in February 2016 Presbyterian Medical Center in Los Angeles, announced they paid 40 bitcoins ($17,000) for the release of the hospital’s computer system. Once a system has been corrupted, there is little that can be done, and even when the ransom is paid, there is no guarantee the files will be decrypted. Unfortunately, the devastation of ransomware is expected to grow as this malicious malware sweeps through cyberspace preying on the vulnerable.
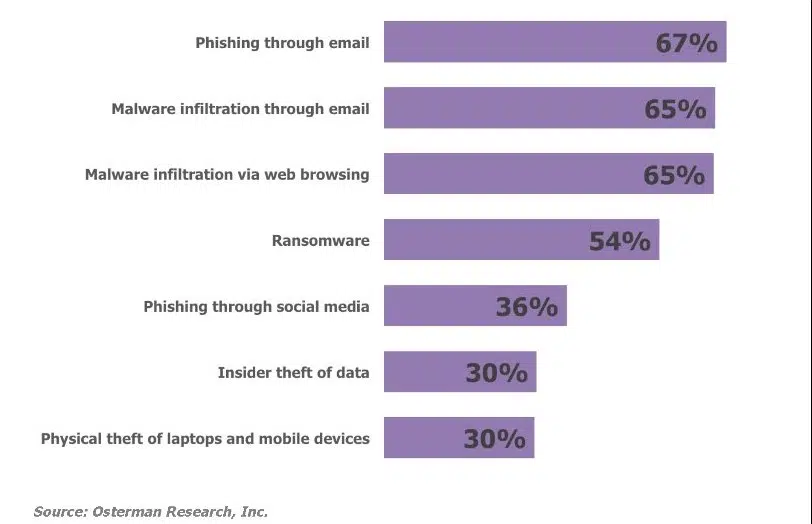
So, how exactly are individuals and companies targeted? Cybercriminals use various techniques to scam users. One way is through phishing. Victims are targeted through fraudulent email. Once the victim opens the fraudulent email and downloads the attachment, the virus is instantly spread through their computer and any other computer associated with that network. Spear phishing is a more sophisticated version of phishing, and is used to target specific users through personalized emails that appear legitimate. Malvertising, advertising on a legitimate website, is another way ransomware is being spread. With malvertising, the ad appears to be legitimate, but once clicked on, the virus instantly downloads. Users are also being infected by visiting compromised websites and joining infected networks.
According to an Osterman Research Survey Report published in August of 2016, phishing is the number one resource used to spread ransomware.
Tips on How to Avoid Ransomware:
- Never click on a link through your email without confirming the email is legitimate.
- Ensure security software programs have been updated with the latest security patches.
- Always back up your data.
- Do not click on pop-up advertisements.
- Stay away from untrustworthy websites.
- Always proceed with caution.
Businesses and individuals that do not have an effective backup and recovery plan will be the ones who will have no other choice but to pay the ransom. The process of backing up data is a critical component of a disaster recovery plan. Backup refers to the copying of important files to a secondary site for preservation in case of a catastrophic event.
There is little that can be done to stop the spread of ransomware once a computer system has been infected, but there are effective solutions, provided by IT Support Guys, that will protect you against it.
- Safe, streamlined data backup and recovery with secure data encryption to prevent unauthorized access
- Data availability through secure storage solutions which eliminate a single point of failure in the data path
- Complete on-premise and cloud backup solutions
- Increased productivity resulting from employees’ ability to access data from any location
- Fast recovery of your data, with minimal downtime, allowing you to get back to overseeing your business
- Simple administration of solutions that are easy to deploy and manage
- 24/7 monitoring
Without a backup service, your small business is at high risk of losing critical data, employee productivity, and revenue. With IT Support Guys backup and recovery solutions, you’ll have the peace of mind that comes with knowing your critical data is safe and secure, and that you have effective recovery methods in place in any event.
Learn more about our network security services or contact us by phone at 855-4IT-GUYS (855-448-4897).