Editor’s Note (May 2025):
When we first published this article in 2018, Unified Threat Management (UTM) was the gold standard for securing business networks. Fast forward to today, and the way we work has been transformed by the cloud, hybrid work, and an explosion of SaaS apps. Perimeter-based defenses can’t keep up. We’ve updated this article to reflect the current state of network security and how cloud-native, zero trust solutions like Next Perimeter’s platform provide protection everywhere your people and data operate.
The Legacy of UTM—And Why the World Has Moved On
UTM was a breakthrough: a single appliance bundling firewall, intrusion prevention, web filtering, and VPN services. For years, it provided effective, simplified protection for office-centric businesses.
But 2018 feels like another era. Today’s world is radically different:
- Work happens everywhere—offices, homes, coffee shops, airports.
- SaaS-powered teams rely on cloud apps, not on-premise servers.
- Cyber threats have become more sophisticated, often targeting identities and cloud data.
- Remote and hybrid work are the new norm, making traditional perimeters obsolete.
The classic UTM box can’t protect what it can’t see—users and data that are always in motion.
The Limitations of On-Premise UTM in 2025
Fragmented Protection
UTM was designed for a world where everyone was in the office. It struggles to secure remote users, cloud applications, and mobile devices.
Complexity and Maintenance
Appliance sprawl, manual patching, and endless VPN troubleshooting drag down IT teams and leave gaps in coverage.
Blind Spots for Modern Work
Traditional VPNs are clunky, hard to secure, and often create more risk than they resolve. Attackers exploit these weaknesses every day.
The Next Step: Cloud-Native, Zero Trust Network Security
Today’s organizations need security that follows users and data—not the other way around. Next Perimeter’s platform was built for this new reality.
What’s Changed?
- No more appliances: Security is delivered through the cloud, not locked in a box.
- Zero trust everywhere: Every user, device, and connection is authenticated and authorized—on any network, anywhere.
- Unified management: Your policies, protections, and visibility are centralized and always up-to-date.
Meet the Modern Platform: SASE, ZTNA, and MXDR
SASE: Secure Access Service Edge
Think of SASE as the next-generation UTM—built for the cloud. It combines firewall, threat prevention, secure web gateway, and private access into one global platform.
- 50+ worldwide points of presence for high performance and compliance.
- Built-in identity awareness that integrates with your Microsoft 365 or Google Workspace.
ZTNA: Zero Trust Network Access
ZTNA replaces legacy VPNs. Access is granted only after verifying the identity, device, and security posture—every time, for every connection.
No static tunnels, no risky “trusted” networks—just secure access, wherever your team is.
MXDR: Managed Extended Detection & Response
We unify endpoint, cloud identity, and network monitoring—delivering 24/7 detection, response, and threat hunting for your business.
Our AI-driven platform proactively hunts for threats, so you’re only alerted to real risks, not false alarms.
The Benefits for Today’s Businesses
For SaaS-Powered Teams and Modern Organizations:
- Protection that follows your people and data—no matter where work happens.
- Eliminate hardware headaches—no patching, no on-site appliances, no manual VPN management.
- Reduce cost and risk with predictable, per-user pricing and zero unexpected infrastructure surprises.
- Faster onboarding, easier management, and peace of mind for your IT team.
Real-World Impact
A mid-size SaaS business migrated from a legacy UTM and VPN model to Next Perimeter’s cloud-native platform. The result?
- 70% fewer IT tickets
- Simplified employee onboarding
- Zero security incidents since migration
Law firms, financial services, and founder-led SaaS businesses have all seen the same: less complexity, better protection, and more time to focus on what matters.
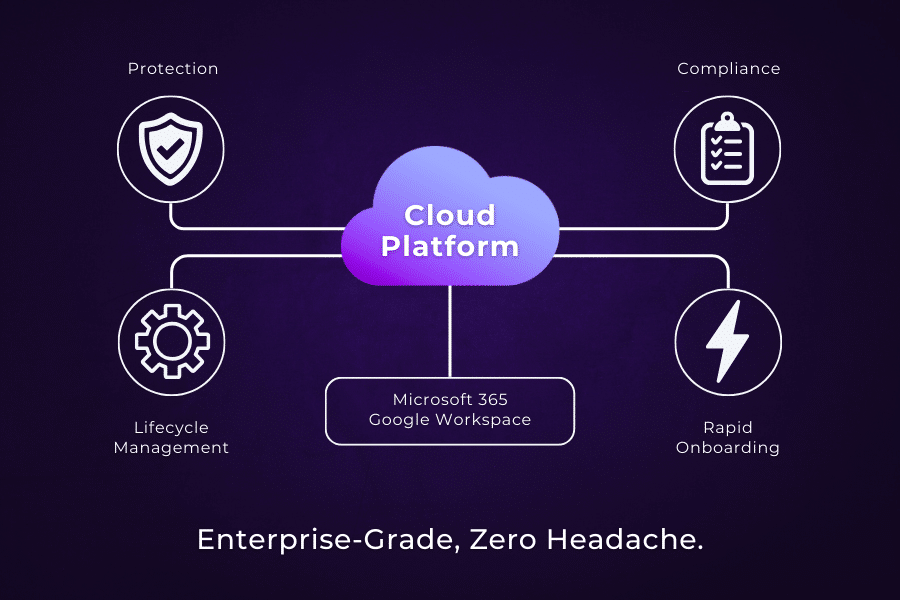
Why Next Perimeter?
- Enterprise-grade protection without enterprise headaches.
- Security, compliance, and lifecycle management—all managed for you.
- Seamless integration with Microsoft 365 and Google Workspace.
- Rapid onboarding with proven blueprints for modern business.
Ready to See What’s Next?
Your business doesn’t live behind a perimeter anymore.
Isn’t it time your security caught up?
Schedule a demo or get a cloud risk assessment today.
Looking to simplify device lifecycle management or modernize your desktop experience?
Learn more about our Lifecycle Management and Modern Desktop Experience solutions.
Still have questions?
Contact our team to see how easy network security can be in the cloud era.
This article was originally published in 2018 and updated in 2025 to reflect current best practices in cloud-native security and zero trust networking.