Most people today spend a lot of time on the Internet, which means that most people spend a lot of time using a browser. Little do they know, selecting the wrong one could easily put their cybersecurity at risk, along with dozens of other actions. For this week’s tip, we’ll go over how to make your Internet browser as secure as possible.
Enable Security Updates (And Turn on Notifications)
We can safely say that the more up-to-date a browser is, the more secure it is going to be because many updates address and enhance the browser’s security features, including any anti-phishing, anti-malware, and plugin security measures. You should also turn on your browser’s automatic updates, which will let you know whenever an updated version is available and will help protect you from security vulnerabilities.
Customize Your Security Settings
Always review your security and privacy settings and make sure your browser settings are as strict as possible. Here are some standard and advanced settings to check:
- Cookies – – Disable third-party cookies, or only enable them if you trust the website and they are required.
- Pop-Up Windows – Block them from opening automatically on a web page, only enable them for trusted websites, or have the browser ask for confirmation
- Block Reported Attack/Fake Sites – If it is available, block malicious sites by enabling this feature
- Camera and Microphone Usage – Block from running automatically, and have the browser ask for confirmation
- JavaScript – Block from running automatically, only enable it for trusted websites, and have the browser ask for confirmation
- Plugins and Add-Ons – Block from running automatically, or have the browser ask for confirmation
Don’t Save Passwords in Your Browser
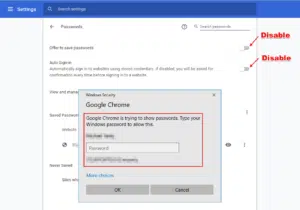
Did you know that anyone with your desktop password can access your saved browser passwords in Chrome? As you’ll see below, it doesn’t require a tech guru to access your password IF you give an individual access to your Windows profile.
Shocking, we know! If you’re serious about web browser security, navigate to the top-right and click the three-dot menu icon in Google Chrome. Next click “Settings,” then click “Passwords,” delete your passwords (if needed open and save your passwords in a temporary password protected spreadsheet), and disable the following:
- “Offer to save passwords”
- “Auto Sign-in”
At IT Support Guys we recommend using a password manager like LastPass or KeePass. LastPass is feature-packed and offers an intuitive easy-to-use interface. While Ninite KeePass offers complete password database encryption using SHA-256, a cryptographically secure method of encryption without any known successful attacks. IT Support Guys recommends using KeePass because the software remains isolated on your local machine versus the cloud, in the (albeit unlikely) event that another online password manager was compromised, you can rest easy knowing that your KeePass passwords were not compromised. Helpful Hint: You can take advantage of KeePass’ hardened security on the go by dropping the encrypted password database file in Office 365 OneDrive if you work from multiple computers, like a work laptop and a home desktop.
Be Cautious When Installing Browser Extensions and Add-Ons
Chrome Extensions and Mozilla Firefox Add-ons can increase your productivity; however, do use discretion when installing. Not only can having 15 Chrome extensions consume a significant amount of your computer’s memory (multitasking ability) but you may unnecessarily increase your vulnerability. While most extensions are safe, it’s smart to research an extension or add-on before adding to your browser. Double check if a new company recently acquired the plugin. The practice of a malicious entity offering to buy a Chrome extension and then adding malicious code to the source is not a new one.
The Chrome extension “YouTube Queue” which allowed users to queue multiple YouTube videos to view later was removed from the Google Web Store in June because it was found intercepting user traffic such as search engine queries meant for Google and redirecting to a spam search engine “Vine.” The malicious extension abused the Web Request API with the intent to generate revenue by serving malicious ads and affiliate links related to the initial query.
Similarly, PC Mag reported earlier in June that an anonymous group of hackers were able to infiltrate and upload a malicious version of the popular Chrome extension for Mega.nz, a cloud storage service. This compromised extension was designed to covertly steal passwords from webpages like Microsoft, Google, and Amazon.
Leverage Antivirus
Is antivirus perfect? No. Is it better to use it? Absolutely. An up-to-date antivirus solution can provide quite a strong defense against most malicious websites or code, and their threat definitions can be updated automatically, meaning that it would only get better and more effective over time. For your company, your antivirus should be centrally managed, not installed on each device.
Use a Limited Account
Instead of using your administrator account for your daily use, consider creating a secondary one with limited privileges to use instead. Many threats leverage the access of the user to deliver whatever payload they have, so the less access the user has, the better. An administrator account is only necessary when you’re making changes to the device, so limiting its use won’t be an inconvenience.
Browser Compartmentalization
There are many different options out there for web browsing – far more than just the likes of Chrome, Edge, and Safari. There is also nothing to restrict you to only using one, which is why another means of improving your security exists: browser compartmentalization.
Browser compartmentalization is a strategy that where uses make use of multiple browsers, assigning certain activities to each. For example, you might only log into key online accounts with Browser A, while Browser B is reserved for general browsing (with its history and cookies disabled), and online shopping is restricted to Browser C. By segmenting your traffic across browsers, you will decrease your vulnerability from a risky click or a malicious add-on.
Try a Browser Made for Security
Many browsers are designed with their security as the top priority. There’s Firefox, for instance, which can be customized to be security-centric, as well as a few open-source versions, like GNU IceCat, Waterfox, and Pale Moon. If you’re more used to Google Chrome, there are secure browsers based on Chromium, the code base behind Chrome. These include Iridium Browser, Ungoogled Chromium, and Microsoft’s Chromium Edge Canary and Development build released in April (updated daily).
Remain Anonymous and Protect Your Traffic with a VPN
Last month we discussed what a VPN is and the benefits of using one. A VPN (short for Virtual Private Network) takes your Internet activity and conceals it behind encryption, boosting your security considerably. There are many VPN services out there, so you will want to lean on a trusted resource like IT Support Guys to help you select and implement one that best fits your needs.
Secure Your Browser with IT Support Guys
Establishing internet security best practices and cultivating safe browsing habits will help protect your business. Just as investing in the right technology and managed IT solutions partner ensures your employees stay up-to-date on the latest online security trends, apps, and security features like antivirus. Educating our visitors and customers are just two ways IT Support Guys seeks to create a more tech-savvy community. We continue to provide Managed IT Solutions for small to mid-sized businesses in Tampa and Los Angeles. Call us today at 855-4IT-GUYS (855-448-4897) and discover how our unlimited support plans help support smart, hyper-growth focused organizations.