SAAS APP SECURITY
Lock Down SaaS Risks Without Locking Out Your Team
SaaS applications boost productivity, but they can also expose sensitive data. Our Zero Trust approach protects your critical apps—like Microsoft 365, Google Workspace, and Salesforce—from data leakage and unauthorized access, ensuring security that’s seamless for your team and strong for your business.
Stronger SaaS Security, Zero Productivity Trade-Offs
SaaS security shouldn’t come at the cost of efficiency. With automated access controls, real-time monitoring, and built-in compliance tools, you can eliminate security gaps while ensuring a seamless experience for your team. Protect sensitive data, stop unauthorized access, and keep your business running—without adding friction to everyday workflows.
Regain Control Over the SaaS App Sprawl
Unmonitored SaaS growth leads to shadow IT, unmanaged accounts, and security blind spots. Our platform centralizes authentication and policy enforcement, giving IT full visibility and control over every app in your environment.
Reduce Password-Based Vulnerabilities
Stolen credentials are the number one cause of SaaS breaches. Reduce risk with SSO, MFA, and continuous authentication, ensuring that only the right people have access—without relying on passwords alone.
Boost Productivity with Seamless Security
Reduce disruptions with intelligent authentication that keeps your team moving without compromising security. Adaptive policies ensure seamless workflows while maintaining strong protection against unauthorized access.

97 Net Promoter Score®

2+ Million Incidents Resolved

4.9 Stars Average Rating

4 Minute Average MTA

94.53% Same Day Resolution
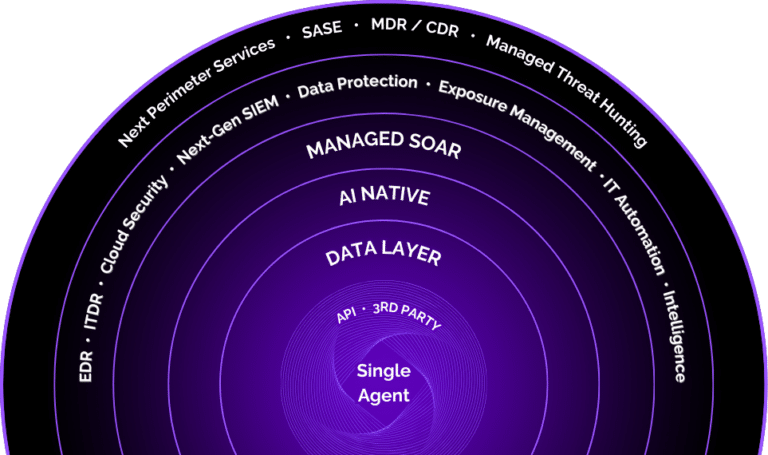
Achieve Total Security with Our Single-Agent Solution
Simplify your cybersecurity with a unified platform that combines advanced threat detection, data protection, and cloud security, ensuring seamless and comprehensive protection.
Zero Trust Access Controls
Every Login Verified — Every Time
Traditional security trusts too much. Our Zero Trust model continuously verifies users, devices, and context before granting SaaS access. Enforce risk-based policies that adapt dynamically to threats, ensuring only authorized access at all times.

SSO & MFA: Strong Security, Fewer Logins
Secure Access Without Extra Complexity

Automated SaaS Risk Detection
Stop Cyber Threats Before They Start
Misconfigured SaaS apps are an open door for attackers. Our continuous security monitoring detects risky settings, overprivileged accounts, and suspicious activity—so you can fix vulnerabilities before they become breaches.

Frictionless Integration with Your Apps
Security That Works Everywhere You Do
Your team relies on dozens of SaaS apps daily. Our solution integrates with Microsoft 365, Google Workspace, Salesforce, Dropbox, just to name a few—enforcing security without disrupting workflows.

READY TO TRANSFORM YOUR CYBERSECURITY?
Switching to Next Perimeter is Simple, with No Downtime or Disruptions
1. Free Exploratory Consultation Call
Let’s dive into your specific needs, security challenges, and current technology set-up. We’ll collaborate with you to start crafting tailored solutions that align with your business goals.

2. Identity & Device Assessment
Our experts will begin developing a customized proposal for your unique environment. We’ll perform a thorough assessment to finalize the scope, ensuring every aspect of your digital security is covered.

3. Schedule Your Seamless Onboarding
With your approval, we’ll launch your onboarding process. Our all-in-one security solution will seamlessly integrate into your existing infrastructure, implemented by our expert team for a smooth transition.
Your Questions Answered: SaaS Security
Learn how Next Perimeter’s cloud-first SaaS Security solutions streamline and protect your digital environment.
What is SaaS Security, and why is it important for my business?
SaaS Security encompasses the measures and protocols designed to protect data, applications, and user access in cloud-based environments. For businesses leveraging SaaS applications, it ensures that sensitive information remains secure, compliance standards are met, and cyber threats are actively mitigated.
How does SaaS Security protect against cyber threats like phishing and malware?
Our SaaS Security solution utilizes AI-driven threat detection and a 24/7 Security Operations Center (SOC) to monitor and respond to threats in real-time. This approach helps prevent malware, phishing attacks, and insider threats, providing a proactive defense against cyber risks.
What role does identity and access management play in SaaS Security?
Identity and Access Management (IAM) is essential in controlling who can access your SaaS applications. Our solution offers advanced IAM features like multi-factor authentication (MFA) and single sign-on (SSO), which strengthen security by ensuring that only verified users can access sensitive data, while also simplifying the login process.
How does data encryption work in your SaaS Security solution?
Our SaaS Security includes comprehensive data encryption, both at rest and in transit, using trusted tools like Intune and BitLocker. This end-to-end encryption ensures that data remains protected across devices and in the cloud, reducing unauthorized access and maintaining compliance.
Can SaaS Security solutions help with regulatory compliance?
Yes, our SaaS Security solution simplifies compliance by providing detailed audit and compliance reporting tools. These reports help businesses meet industry standards such as HIPAA, SOC2, and others, enabling easy tracking and documentation for regulatory requirements.
How does threat detection work within a SaaS environment?
Our SaaS Security leverages AI and machine learning to continuously monitor for suspicious activity. When a threat is detected, the system triggers automated responses to contain and mitigate risks before they can impact your operations, with round-the-clock support from our Security Operations Center (SOC).
Can I integrate SaaS Security with my current security tools?
Absolutely. Our SaaS Security solution is designed for seamless integration, allowing you to unify your security infrastructure and gain comprehensive visibility. This integration supports a broad range of security tools, ensuring cohesive and efficient protection across all platforms.









