SIEM & THREAT DETECTION
See Everything. Detect Faster. Protect Smarter.
Enterprise-grade threat detection shouldn’t be reserved for large corporations. Our SIEM solution, designed specifically for SMBs, gives you the powerful visibility you need without the overwhelming complexity. Integrated into our platform, it makes it simple to monitor your entire IT environment, detect threats early, and protect your business.
Unlock the Power of Next-Gen Threat Detection with SIEM
A strong cybersecurity foundation starts with knowing what’s happening in your business at all times. Next Perimeter’s SIEM provides full visibility across your IT environment, helping you detect threats early and respond before they cause damage. Whether it’s monitoring endpoints, networks, or cloud applications, our solution ensures you stay in control of your security without the hassle of complex configurations.
Detect Threats Instantly with Proactive Monitoring
Cybercriminals move fast, but Next Perimeter’s SIEM moves faster. Our platform continuously scans your IT environment, detecting suspicious activity in real time and stopping potential threats before they can disrupt your business. By identifying risks early, you can prevent breaches and avoid costly downtime.
Full Visibility into Your Entire Security Landscape
If you can’t see it, you can’t protect it. Our SIEM collects and analyzes data from endpoints, cloud applications, and user activities, giving you a centralized view of your entire security landscape. You can quickly identify vulnerabilities and strengthen your defenses before attackers take advantage.
Simplified Compliance and Reporting
Meeting compliance requirements doesn’t have to be a burden. Next Perimeter’s SIEM automatically logs security events and generates reports to help you stay aligned with regulations like HIPAA, GDPR, and PCI-DSS. With built-in compliance tools, you can simplify audits and prove your security posture without extra effort.

97 Net Promoter Score®

2+ Million Incidents Resolved

4.9 Stars Average Ratings

4 Minute Average MTA

94.53% Same Day Resolution
Achieve Total Security with Our Single-Agent Solution
Simplify your cybersecurity with a unified platform that combines advanced threat detection, data protection, and cloud security, ensuring seamless and comprehensive protection.
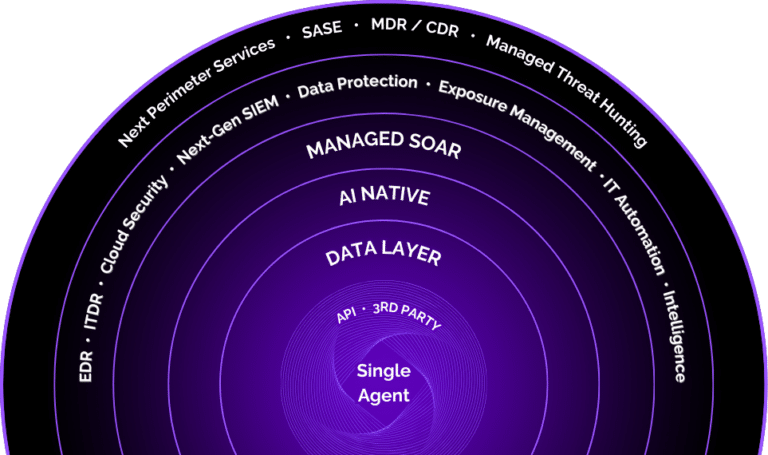
Protect Your Organization From Cyber Threats with SIEM & Threat Detection
Advanced Features to Strengthen Your Security
Easy and Hassle-Free Deployment
Get Up and Running Without Downtime
Deploying a security solution shouldn’t slow your business down. Our SIEM is pre-tuned for SMBs and works right out of the box, so you can start monitoring threats immediately—without complex setups or lengthy onboarding processes.

Straightforward and Affordable Pricing
Enterprise-Grade Security Without the Enterprise Cost
Security shouldn’t break the bank. Next Perimeter’s SIEM is included in all plans with no hidden fees or unexpected costs. Get powerful threat detection and compliance support at a price that makes sense for growing businesses.

Fully Integrated Security Ecosystem
Seamless Security Across All Your Essential Tools
Our SIEM works effortlessly with Next Perimeter’s SOAR, MXDR, and SASE solutions, giving you a fully integrated security ecosystem. No need for disconnected tools—everything works together to strengthen your defenses and streamline security operations.

Custom Alerts for Better Threat Detection
Cut Through the Noise and Focus on Real Risks
Too many security alerts can be overwhelming. Our SIEM fine-tunes alerts to your specific environment, reducing false positives so you can focus on the risks that matter most. Stay informed without getting bogged down by unnecessary notifications.

Automated Reporting for Compliance
Stay Secure and Meet Regulations with Ease
Whether you need to comply with HIPAA, GDPR, PCI-DSS, or other regulations, our SIEM has you covered. With built-in log retention and automated reporting, you can meet security standards without the manual work or added stress.
READY TO TRANSFORM YOUR CYBERSECURITY?
Switching to Next Perimeter is Simple, with No Downtime or Disruptions
1. Free Exploratory Consultation Call
Let’s dive into your specific needs, security challenges, and current technology set-up. We’ll collaborate with you to start crafting tailored solutions that align with your business goals.

2. Identity & Device Assessment
Our experts will begin developing a customized proposal for your unique environment. We’ll perform a thorough assessment to finalize the scope, ensuring every aspect of your digital security is covered.

3. Schedule Your Seamless Onboarding
With your approval, we’ll launch your onboarding process. Our all-in-one security solution will seamlessly integrate into your existing infrastructure, implemented by our expert team for a smooth transition.
FAQ: Security Information & Event Management (SIEM)
Get answers to common questions about our SIEM solutions, threat detection, and how Next Perimeter can enhance your security strategy.
What is SIEM, and how does it benefit my organization’s security?
SIEM (Security Information and Event Management) is a technology that provides real-time monitoring, analysis, and threat detection across your network. By collecting and analyzing log data from multiple sources, SIEM identifies potential threats and enables rapid responses, enhancing your organization’s overall security posture.
How does Next Perimeter’s SIEM solution help reduce alert fatigue?
Our SIEM solution prioritizes alerts to filter out false positives, allowing your team to focus on genuine threats. This targeted approach minimizes unnecessary notifications, reducing alert fatigue and ensuring that only the most critical issues require attention.
Can your SIEM and Threat Detection solution integrate with my existing infrastructure?
Yes, Next Perimeter’s SIEM is designed for seamless integration with your current infrastructure. Whether your business is scaling up or adapting to new security requirements, our solution can integrate easily, allowing for a hassle-free deployment that grows with your organization.
What kind of visibility does SIEM provide into potential threats?
Our SIEM solution offers comprehensive monitoring and visibility across your network, continuously scanning endpoints for signs of threats. This full-spectrum visibility helps detect cyber risks early, so that our team can take swift action to protect your business.
How does Next Perimeter’s SIEM handle data storage and retention?
Our SIEM solution uses retention-based billing with unlimited storage, allowing you to control storage based on your needs. You only pay for the devices you use and the retention period you choose, with no worry about log volume or data storage limits.
What are custom dashboards, and how can they improve our security management?
Custom dashboards provide a tailored view of your security landscape, allowing you to monitor critical metrics, track trends, and generate insights specific to your organization. With these tools, your team can make data-driven decisions to enhance your security strategy and respond proactively to emerging threats.
Does Next Perimeter’s SIEM offer real-time threat intelligence?
Yes, our SIEM solution integrates real-time threat intelligence, utilizing global insights to enhance proactive defense. This integration allows us to detect and mitigate risks swiftly, keeping your organization ahead of evolving threats.









